Cyber Security: Offensive Mindset - Sprint 1
Week: 4th February
Introduction
Cyber Security has always been interest of mine since meeting the Cyber Security Society at UTS. Unfortunately enrolled as a Software Engineering and Japanese student I am limited to enrolling in varying array of elective subjects including Cyber Security related subject. Fortunately, at the end last year, UTS offered a 4-week Summer Studio subject and one of the studios was about Cyber Security.
This was exiting to apply for since this subject can be credited for 6 credit points and be listed on my academic transcript for my employees to see. Fast forward few months later, my application was a success and the first sprint of four is completed.
Expectations (so far)
Our tutor Larry has been a great vacillator of the studio so far by providing enough information on the subjects and extra materials. He has been very transparent with the students from the very start to make his summer studio become open to all person from different backgrounds, skills and personality. From my interpretation, he wants this studio to be ours and wants us to very safe that we can ask questions or ask for help without judgement or intimidation.
The first time enrolling into a Midas Summer Studio my expectation of this type of initiative from UTS has been productive and positive. It fantastic to see that UTS do offer these types of different studios to cater towards a large sum of people who do want to take initiative in their studies and want to make the most of it. The Cyber Security studio does a fantastic job of keeping the students including myself engaged with the presentation and conversation between the tutors. Keeping this high level of interaction makes be believe I can achieve goals I can set out for myself and become a better student by the end on this studio.
Although I have talked about good things about these studios they are some improvements that can be suggested and implemented by the next sprint. Talking to fellow classmates we had a difficult time of creating our group presentation on Wednesday and writing our ‘Sprint 1 Reflection’ due on Sunday Night. This problem was mainly due to the freedom were given by having free rein of presenting or reflecting anything we wanted. This impacted on our progress by having to focus on the key topics and research different methodologies of presenting and writing reflections. This was quickly resolved by asking questions through the Microsoft Team and personally messaging the tutors. They could provide enough information that was precise and informative for us to proceed with our submission.
Talking to peers during high school and through our university experience I believe the biggest problem we have today is studying a suitable degree for a job in future that may not exist. Often, I have friends who struggle with the idea of identifying a suitable career path for themselves. Made unclear by the lack of exposure to real life industrial experiences it’s great to have an opportunity to witness people like Rob talking about their career. It becomes a valuable insight to our future by providing us connections to people who do cyber security for a living.
Group Reflection (Wednesday Presentation)
On Monday, we quickly transitioned into studio and formed groups. The group was 5 students and we called the SSHC (Super-Secret Hacking Club). The students in our group are Jason, Vishal, Frank, Andy and me. Our task is to create a small 5-minute presentation on any topic on security. Collectively we brainstormed ideas and choose the best one that stood out the most. The topic we deciding to present on was bug bounty and specially HackerOne’s bug bounty that was recently solved about Valve’s Steam Key Bug. It was a bug that if a user was using a developer account for Steam Marketplace, they could reach the endpoint of a certain file that will generate an unused key to any Steam Game.
We all collaborated during the first day to create slides and keynotes we can use to write our speeches on Tuesday. The team had another meeting the next day to create and finalise the presentation for Wednesday. From early observation of the team, we have great communications and understanding our tasks to complete this presentation.
Introduction of SSHC

My slide on the impact of bug bounty and the vulnerability found
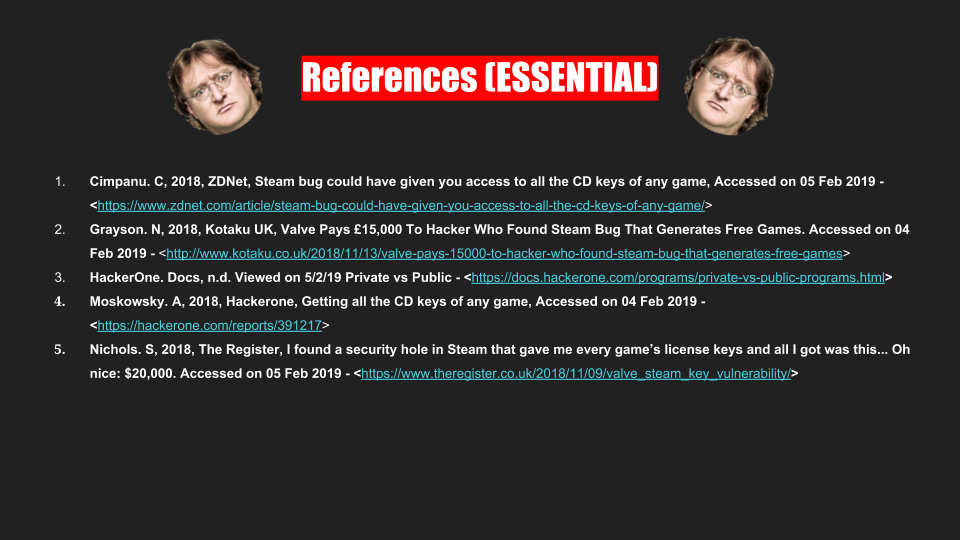
The references we used for the presentation
My part of the presentation was the impact of this bug if it was publically known on the dark web and possible exploitation of the bug. The main stakeholders of the bug were Valve, the developer of the game that the key generated and the customer who buys the key if it was sold. The effects of the bug can be detrimental to all the stakeholders by the loss of profit through the unauthorised generation of keys. Valve has contracts with developers along with policies and guidelines that help the transaction of profit go easy between companies. Valve currently takes a 20% profit for every game that a developer puts up on their store in return customers can view and buy their game on the most popular game market store in the world. However, the effects the bug makes this contract null as all profits would be 0% if the games were given out for free by a hacker exploiting this bug. Some hackers may want to exploit this bug by profiting off it by selling this keys to third party digital key stores like GOG and G2A who was recently found selling games from stolen credit cards. The non-profit of the games can lead game studios to become bankrupt and leave their employees unpaid.
This possible impact of this bug is why bug bounties were created in the first place. Crowdsourcing bug bounties is a solution to minimise the possible negative impacts.
(current) Challenges
The Wednesday presentation presented many challenges that I would address in early in the studio in hopes to improve or solve by the end of sprint 4. Public speaking has always been an issue of mine personally since at a young age. I believe this was due to my reserve personality being much introverted and shy that started young age and stay with me until today. The challenges that come with public speaking was clearly speaking at audible tone, the ability to pronate words without slurring, eye contact with the audience and remembering your speech. These problems can be generalised to being nervous. Anxiety can get worst out you but it allows you to assess the importance of a certain matter. To overcome this nervousness is a challenge that can only be solved through the constant exposure to being force talk in front of a crowd. In addition, I can creative think of strategic ways that can improve the way of speaking like practicing beforehand or writing down key words to jog my memory. By the end studio, I hope improving public speaking will allow me to answer questions in my job interviews with a high level of communication a technicality.
The next biggest challenges I have is time management. Living in suburbs where commuting from your house to university takes 1.5 hrs each way there is a lot of preparation that should be done to be punctual.
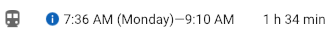
Screenshot from google maps of my commuting time.
Although I have been in the Cyber Security Society for almost more than a year, I haven’t dedicated much time to studying Cyber Security either doing CTFs or doing training like PentesterLab. This became more apparent on Friday when I became frustrated when I couldn’t penetrate the OWASP Juice Site using XSS or SQL injection. Being unable to solve these simple challenges will become a roadblock if I am not willing to put the time in learning pentesting.
Goals (over the month)
I have many goals for myself over the month which include short and long term goals. These goals mainly focus on issues that I have currently experiencing before the start of the studio and during it.
My short-term goals are to improve my interpersonal and technical skills to such a level where I can confidently interact with members with more knowledge and expertise in cyber security. These short-term goals include:
- Improving public speaking
- Develop a sleep schedule
- Learn something new every week and tell someone about it
- Ask students or tutors to give you honest opinions about my weakness I don’t recognise
My long-term goals encompass completing majority of my short terms to achieve self-discipline to allow me to develop a habit to become effective and efficient in completing tasks at hand. These goals cannot be completed during a short time only through a substantial amount of time passing. The build-up of completion of these goals is to confidently answer and ask questions in job interviews and successfully being recruited by a cyber security or software development team. My long-term goals are:
- Recruited by a company
- Able to teach others
- Completing varying tasks before a deadline
- Maintain a high-level of competency
Conclusion
Overall, it’s a exiting to see the subject unravel to us and to become slowly more certified in cyber security each week until the completion of the studio. I believe if Larry and the tutors keep up the same degree or more of enthusiasm and positivity during the studio it we make us more eager and engaged to learn.