Cyber Security: Offensive Mindset - Bug Bounty
Due: 13th February
Introduction
Bug Bounty is a platform that rewards individuals who discover a vulnerability or bug in a system to limit the potential risk of an organisation. This platform can any be closed internally within a company however crowdsourcing is one of the most popular method of promoting bug bounties. This platform has been proven a success with HackerOne helping companies since 2012 discovering over 72,000 vulvnerabilites and paid out $23.5 million to hackers as of December 2017. [0]
If a security vulnerability has been found, there are disclosures and guidelines a hacker must consent to before submissions can be made to minimise the risk of exploitation of vulnerabilities. These principles are commonly known as Responsible Disclosure Policy.
A responsible disclosure policy states:
- What part of the system are in-scope and out-of-scope.
- The vulnerabilities and bugs that are accepted from submission.
- An exclusive email address for reporting the issue.
According to CERT Australia a Vulnerable Disclosure Policy ‘will also provide vendors and developers with additional time to mitigate the vulnerabilities and enable affected systems of national interest to reduce their exposure’.
How ethical hacking and bug bounties are impacting stakeholders.
Ethical hacking is highly sought and evident in the industry where it has become a popular career path of today. These hackers are commonly known as white hats who performs tasks of a malicious hackers without the exploits and risk. HackerOne’s disclosure describe what an ethical hacker (finder) should do and their policy, ‘Do no Harm’, states how one should act. These type of policies ensure that participates of such programs and professionals in the industry do not reap the benefits of an exploitation without knowledge of a company.
Responsible disclosures policies are created and enforced to limit the the risk of black hats hackers who did not agree or obey such guidelines and ethical practices. Their acts often comes under illegal acts and often puts hackers in a bad light and often generalised by the vast majority of news networks, social media and entertainment industry that all hackers are criminals. However, there are hackers with the right mind-set and morality who act by principle and are genuine people who it for the greater good.

Screenshot HackerOne's Vulnerability Disclousre Philosophy
This lawful offensive mind-set is one of the reasons that allows bug bounty platforms to exist today and will continue until a newer popular method of discovering way vulvnerabilities is created. Hackers of this kind of platform benefit stakeholders by securing their assets and most importantly help make themselves become better hackers of tomorrow.
The most significant security stakeholder of any other organisation are often their clients. The protection against data breaches and exploitation of personal information vulnerabilities are classified the most important aspect of security. Any lost or breach of private information can affect the lives of clients and can potentially fine companies millions to billions for their unsecure network.
Lately, data breaches are becoming so common in the last couple of years that the ICO, Information Commission’s Office of the UK, that the average fine for data breaches have doubled in just a year [1]. The exponential rise of breaches is leading a new surge of ethical hacking where companies have created and enforced stricts policies that include the use of internet on their network, usage of personal devices and other measures to decrease the risk of threats and attacks from hackers. However, many smaller businesses do not have access or knowledge to design and create such policies to reduce their risks against attacks which put many businesses at risk.
On another note in 2018, Australia proposed and passed a bill called the ‘Assistance and Access Bill 2018’ infamously known for its controversial laws to grant access to encrypted data. This bill grabbed the attention of the security audience globally where individuals declared their opinions of their rights of privacy and protection of personal data. The BBC news published an article of this issue which highlights a tweet of a programmer in Australia who stated ‘I have an ethical obligation to users of my software not to expose their data’ [2]. These concerns have been on a rise in Australia since the passing of such law were depicted to be national threat to all citizens of Australia.
Overall, bug bounty is a great creative solution to protect data however it’s a just a band-aid to the problem. Security firms have urged governments for support to enforce smarter and stricter laws and regulation to protect the theft of information however there is little to no work currently being shown by any governments in the world.
How you can implement things you’ve learnt throughout the week to test web apps under a responsible disclosure program.
The most important methodology that I have from experienced worked is designing and deploying a system for a specific need. Implementing this process to test web apps under a responsible disclosure program can allows myself and others in instructional manner to reconstruct a vulnerability from step a to z. Responsible disclosure program only work if an individual who are solving these issues agree putting their career and life on a line if legal issues are to arise. Only these people who want to genuinely want to help can benefit themselves, the company and everyone else to make the digital world safe and secure.
Conclusion
The hacking culture since the 80s has been always been an underground hidden community where individuals who had access to computers were extremely limited and rare. The hacking community at the time was prominently known for their shenanigans of WANK worm, a computer virus which attacked at a global scale and eventually caught NASA by surprise. Since no one at the time thought someone from an external network could access their system, accounts had default usernames and passwords that allowed WANK worm to have a little fun and change them. This was only feasible due no having no laws against real life security threats in the online world in the 80s. [3][4]
However, the fun and niche side of hacking slowly turn against everyone and hackers started to get a bad name. But, fast forward 2019 there is a reconnaissance of ethical hacking where hackers are employed and paid to hack things legally. Referencing the image below, it fundamentally clears there are numerous amount of reasons why people hack and money isn’t the most important. Learning, having fun and being mentally challenge are the top voted answers there reasons to hack. The hacking world is constantly changing and morphing which requires hackers to adapt and creatively think and learn new solutions.
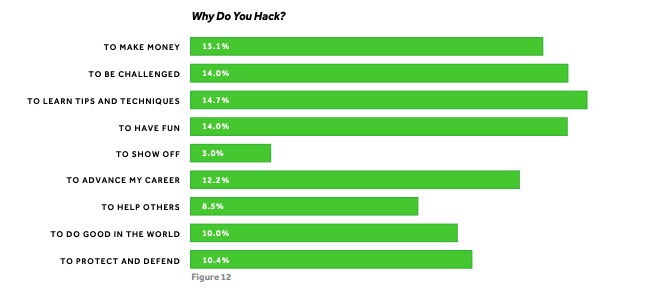
HackerOne's Hacker Report 2018
If you love to hack or dont know how to, or want to make friends with the same mind-set, I encourage you go to a local hacker conference where you get to meet security enthusiasts and professionals who are willing to help you grow and succeed as a hacker.

Hacking the mainframe... I'm in.
References
PROVIDED REFERENCES FROM MICROSOFT TEAM. https://www.hackerone.com/disclosure-guidelines https://www.bugcrowd.com/resource/what-is-responsible-disclosure/
[0] https://www.hackerone.com/sites/default/files/2018-01/2018_Hacker_Report.pdf [1] https://www.information-age.com/data-breaches-fine-123475976 [2] https://www.bbc.com/news/world-australia-46463029 [3] https://www.theage.com.au/national/hack-to-the-future-20030525-gdvriu.html [4] https://www.counterpunch.org/2006/11/25/the-curious-origins-of-political-hacktivism/ [5] https://www.cert.gov.au/critical-infrastructure-big-business/report-incident/vulnerability-disclosure-policy [6] https://www.businessinsider.com.au/hacker-earns-80000-as-bug-bounty-hunter-2016-4?r=US&IR=T
Thanks.