Cyber Security: Offensive Mindset - Web Application Security
Due: 15th February
Task
From Microsoft Team,
Have your defined problem statement on web-application security.
Use your problem statement and the resources provided above to show evidence of web-app vulnerabilities. Were you able to manipulate the content? Where you able to escalate privileges on the web-app? How does it tie back to your problem statement? Have you linked your outcomes and results to any of the SLOs?
More importantly, how do these issues effect a business? How can businesses remediate these issues? How effective are security prevention systems and software development life-cycles?
Introduction
Web-application security is a specific form of information security that’s protects a comprehensive range of web platforms from security vulnerabilities. This type of security is often offered for website owners who uses databases, general software tools and social media.
From the Gartner, a world leader in research, highlights it is estimated that 70% of all security breaches are due to vulnerabilities with the web application layer. That traditional security mechanisms such as firewalls and IDS provide little or no protection against on your web applications.
The problem with web-application security is in global 24⁄7 hr economy it is not viable to afford time and money to fix web application vulnerabilities that can put down your website for hours, days or forever. Even if it was possible to fix all the current vulnerabilities there will be more found in newer updated versions of software frameworks and tools or using a new and upcoming software used by few.
Most major financial service firms have services firms major technical controls, staff and processes in place but many organisations have not yet invested in secure networks and security automation against security attacks. According to Cisco 2017 Annual Cybersecurity Report, ransomware is growing at a yearly rate of 350%.
Common types of Vulnerabilities
The Open Web Application Security Project (OWASP) is an open community dedicated to enabling organisations to develop, purchase and maintain applications and APIs that can be trusted. The OWASP Top 10 is to educate developers, designers, architects, managers, and organisations about the consequences of the most common and most important web application security weaknesses. The Top 10 provides basic techniques to protect against these high risk problems and provide guidance on where to go from here. All though OWASP have emphasizes the Top 10 there are hundreds of vulnerabilities that affects the overall of web application security.
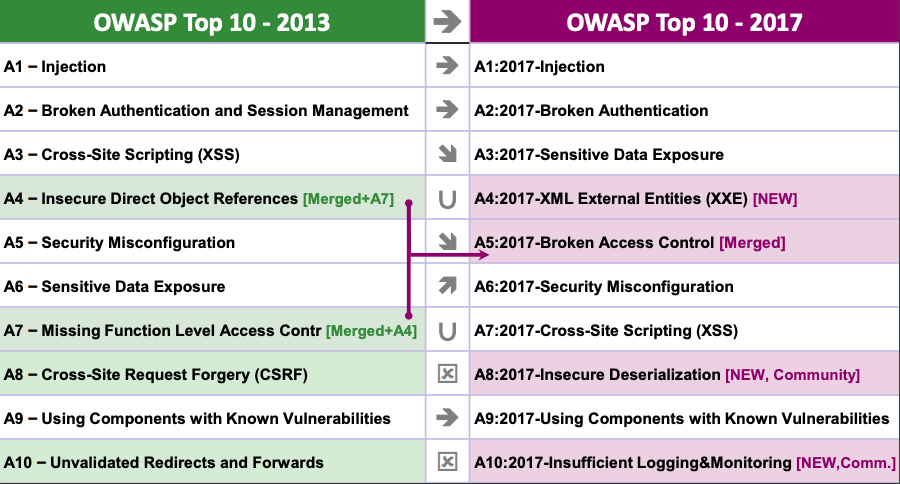
The Top 10 comparison from 2013 to 2017. Credits to OWASP Top 10 2017 PDF.
SQL Injections
A type of web application security vulnerability in which an attacker attempts to use application code to access or corrupt database content. It allows attackers to create, read, update, alter, or delete data stored in the back-end database.
Cross-site Scripting (XSS)
Targets an web application by injecting code, usually a client-side script like JavaScript, into a web application’s output like an address bar or search bar. XSS manipulate the client side script to execute a desired output. Execute scripts can hijack user sessions, deface websites or redirect user to malicious sites. This is common on free downloaded software websites that are littered with fake download buttons and fake advertisement to buy a certain item.
Default Security Settings One of the most simplest form of getting admin access is checking if they release default admin credentials into the production model. This could be done running a script using compiling all the default password from routing and most popular default account settings from online. There are numerous amount of vulnerabilities such as:
- Debugger enabled
- Inspecting site if they left admin credentials in the code
- Unlisted enable directory listings that cant access through the interface
- Outdated software
- Old alert messages
Session Tokens and Data
Everything you use your computer and use your account credentials they are storage for your session to let you be logged into to the web application. However, leaving your account logged in can allow hackers to hijack your session acting as your account on a remote computer and steal your session tokens that store your personal data such as username and password.
Other
- Hidden Manipulation
- Parameter Tampering
- Cookie Poisoning
- Stealth Commanding
- Forceful browsing
- Directory traversals
- Session hi-jacking
- Denial of service
- Information disclosure
- Backdoors and debug options
- Configuration subversion
- Buffer Overflow
- Vendor Option Exploitation
- Access to administration areas and internal modules (Default Settings)
- Improper management of permissions
- XML/SOAP vulnerabilities
- HTTP Attacks
- Clickjacking/UI Redress Attack
XPLOITATION EXAMPLE Ransomware Ransomware is a type of malware that encrypts data making it possible for the owner to gain access to their computers or network without paying the hacker a payment. In some instances owners have paid a large sum of money to receive nothing back except an empty bank account and a locked computer. It would be impossible for an owner to retrieve back there money as payment through cryptocurrency exchanges have been growing in popularity due its paperless trail.
An example of recent ransomware was in 2017 the WannaCry ransomware attack that targeted a vulnerably in Microsoft Windows software where many computers were not updated to latest version of Windows. The results was damages ranging from millions to billers of dollars that affected up to 200,000 computers across 150 countries.
On a side note, the US, UK and Australia have pointed fingers that North Korea was behind the attack even though this exploit was propagated using an existing exploit called EternalBlue and DoublePulsar created by U.S. National Security Agency.
The attack was through a vulnerable SMB port, server message block, that provides access to data, computers and ports on a network; specially through TCP Port 445 and NetBOIS API on port 137 and 138 on UDP/TCP and 190 over TCP/IP.
NetBIOS on your WAN or over the Internet, however, is an enormous security risk. All sorts of information, such as your domain, workgroup and system names, as well as account information can be obtained via NetBIOS. So, it is essential to maintain your NetBIOS on preferred network and ensure it never leaves your network.
Firewalls, as a measure of safety always block this port first, if you have it opened. The port 139 is used for File and Printer Sharing but happens to be the single most dangerous Port on the Internet. This is so because it leaves the hard disk of a user exposed to hackers.
Once an attacker has located an active Port 139 on a device, he can run NBSTAT a diagnostic tool for NetBIOS over TCP/IP, primarily designed to help troubleshoot NetBIOS name resolution problems. This marks an important first step of an attack — Footprinting.
Using NBSTAT command, the attacker can obtain some or all of the critical information related to
A list of local NetBIOS names Computer name A list of names resolved by WINS IP addresses Contents of the session table with the destination IP addresses With the above details at hand, the attacker has all the important information about the OS, services, and major applications running on the system. Besides these, he also has private IP addresses that the LAN/WAN and security engineers have tried hard to hide behind NAT. Moreover, User IDs are also included in the lists provided by running NBSTAT.
This makes it easier for hackers to gain remote access to the contents of hard disk directories or drives. They can then, silently upload and run any programs of their choice via some freeware tools without the computer owner ever being aware. The main reason is was thought to be North Korea was due to a similar exploit through SMB called the Sony Picture Hack in 2014. A hacker group known as ‘Guardians of Piece’ leaked confidential data from the film studio involving personal information of employees, emails, un-released films and other information. This attack was made to demand the withdrawal of the Sony film ‘The Interview’, a comedy film about a plot to assassinate the leader of North Korea. This resulted in the withdrawal screening the movie. The group had no affiliation to North Korea and US found no evidence of it.
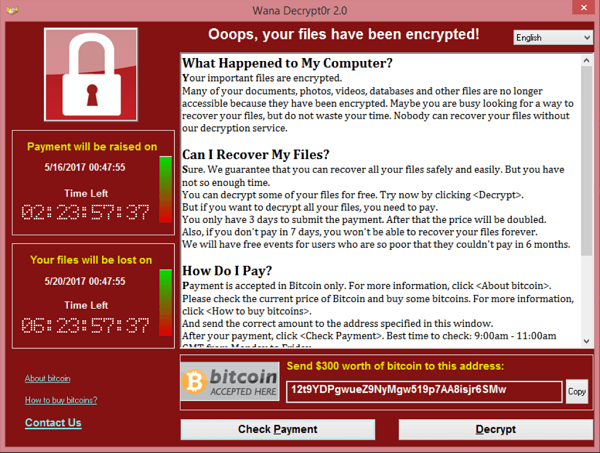 Screenshot of WannaCry deployed on an infected computer. Credits Wikipedia.
Screenshot of WannaCry deployed on an infected computer. Credits Wikipedia.Ransomware is increasing in popularity due is effective way of gaining profit. The payment is entrancement using cryptocurrency and the cost of paying outweighs the cost of losing important documents or a lifetime of work. Usually small payments under $1000USD reasonable for some individuals however paying the hackers only increases the amount ransomware developed and released to the world.
This follows another metric release last week from John Motherly, the found of Shodan search engine that collects data by device type. It found more than 2,300,000 internet connected devices with open SMB ports of which 970,000 are configured for ‘guest access’.
How to fix
So, what can you do? In short order: Stop using Windows on the desktop, use Linux instead. If you insist on using Windows, upgrade to Windows 10 Patch Windows Disable SMB1 Block port 445 on your network firewall.
CONCLUSION
Web applications exploits are most popular way of producing money, ‘Cybersecurity Ventures predicts cybercrime will cost the world in excess of $6 trillion annually by 2021, making it more profitable than global trade of all major illegal drugs combined.’ The protection against these exploits can only be done through the global awareness and promotions of these vulnerably to average user besides people in the technology field. This can be done through the enforcement of training programs that help individuals and companies protect themselves potential attacks. Enforcing bigger fines on companies who hold a large value of their assets in data and providing basic level knowledge to everyone.
SLOS IN A NUTSHELL
-
Stakeholder and identify problem The users of any web application is stakeholder. We can protect ourselves from data breaches by not providing crucial information that could be used for identify thief. Such as not posting information that can be used for security information. This requires any organisations that require not use security questions such as birthdates as they can be easily found on social media.
-
Design thinking identified problem Hackers can apply their current knowledge of exploits in web applications and develop a system that is viable for repetition. Making a write-up for particular problem is a great solution to develop your habit and deepen my understanding of a particular problem. This allows to be to in-depth try certain solutions that can be catered to a certain vulnerability.
-
Technical skills My technical skills are quite broad and basic, I can develop my skills to a higher degree by doing challenges such as Lab Goat and Natas or training problems like PentesterLabs to further progress and accelerate my learning process.
-
Collaboration and communication Not applicable.
- Critical self-evaluation I have learn valuable from this week’s tutors partially Luke who have guided me into direction on where I can focus to learning specific techniques and find things I particularly enjoy. If I am not going gain anything or have fun with it, move on and learn something new.
- Peer review Not applicable.
- Performance evaluation Not applicable. See XSS Vulnerability for further evaluation.
VOCABULARY
| Word | Definition |
|---|---|
| Web-application | An client-side program that is usually viewed through web browsers ran on remote servers. |
| Ransomware | A form of malware that threatens to publish victim’s data or perpetually block access to it by encrpting it unless a ransom is paid. |
| SMB | Server Message Block |
| UDP | User Datagram Protocol |
| TCP | Transmission Control Protocol |
| IP | Internet Protocol |
| NetBOIS API | Network Basic Input/Output System |
| SQL | Structured Query Language |
| XSS | Cross-site scripting |
BIBLIOGRAPHY
https://blogs.cisco.com/financialservices/ransomeware-lessons-for-the-finanical-services-industry https://www.hackerone.com/sites/default/files/2018-07/The%20Hacker-Powered%20Security%20Report%202018.pdf https://cwatch.comodo/security-issues-with-websites.php https://www.owasp.org/index.php/Main_Page https://www.owasp.org/images/7/72/OWASP_Top_10-2017_%28en%29.pdf.pdf https://senseofsecurity.com.au/consulting/web-application-security