Cyber Security: Offensive Mindset - Sprint 2
Timeline: 11th - 17th
Due: 17th February 11pm
INTRODUCTION
This is the end of the second sprint of researching about web application security.
This week’s content was presented by Larry and Darsh to research bug bounties and responsible disclosure policies and with the help of Luke who is currently working for a company called ‘Sense of Security’ whom talked about web pentesting.
Quite reformed in the field, Luke offered us an extensive range of knowledge of web application especially about basic networking of which ports we should remember and how cross-site scripting (XSS) functions.
From Amit Klein, the definitions of 3 types of XSS follows (OWASP 2017):
Reflected
Reflected XSS occurs when user input is immediately returned by a web application in an error message, search result, or any other response that includes some or all the input provided by the user as part of the request without that data being made safe to render in the browser, and without permanently storing the user provided data. In some cases, the user provided data may never even leave the browser (see DOM Based XSS next).
Stored
Stored XSS generally occurs when user input is stored on the target server, such as in a database, in a message forum, visitor log, comment field, etc. And then a victim can retrieve the stored data from the web application without that data being made safe to render in the browser. With the advent of HTML5, and other browser technologies, we can envision the attack payload being permanently stored in the victim’s browser, such as an HTML5 database, and never being sent to the server at all.
DOM-based
DOM Based XSS is a form of XSS where the entire tainted data flow from source to sink takes place in the browser, i.e., the source of the data is in the DOM, the sink is also in the DOM, and the data flow never leaves the browser. For example, the source (where malicious data is read) could be the URL of the page (e.g., document.location.href), or it could be an element of the HTML, and the sink is a sensitive method call that causes the execution of the malicious data (e.g., document.write).”
This section was used for Luke’s homework on Wednesday to find example of real life vulnerability either through CTFs, bug bounties or some means. I had found a HackerOne XSS vulnerability about using DOM-based XSS to inject a .gif file into ‘send-payment’ functionality into a crypto website. I had discussed this XSS injection with Panda and Johnwei who were really intrigued by the thought by inserting a funny gif into the client website. More details.
Over the week we have been given the opportunity to research a particular problem statement with web application security. Mine was, ‘In a 24⁄7 hr economy, how does one viabily protect their application against common vulnerabilities?’. The word ‘common’ is defined by how easy and quickly is it to research a web application vulnerability and attack any web application as you please. I tested this theory by using a quick google and youtube search, ‘easy xss attack’, and applied my knowledge on out-of-date website.
Although bigger organisation such the big 4 banks; CBA, Westpac, ANZ and NAB; have protected their web applications against such threats, what about smaller businesses who do not have a team dedicated to maintaining their assets. Smaller organisations are more susceptible to such attacks as their budget maybe limited to maintain their web application security.
Out-of-dates systems and web application which run older softwares can be exploited by any hacker who can install malware such as ransomware. Malware can be install through insecure web applications that may accept input from client-side browser. It can also be installed by human error by those who aren’t knowledgable about how to spot fake links from websites or phishing emails.
There are a wide range of solutions but are categorised up by how affordable and cost effective it is for an organisation. The main solution to is problem is that should everyone have access free training or knowledge of how to mitigate an issue if there was an attack. By providing knowledge like updating your system regularly and research if your current web application software has any software vulnerabilities, it is a great start in securing any web applications.
What did we do on Monday?
What have I learnt?
- Continued to fix my website
- Changed the color theme of the website to a modern and sleek design
- Learnt about hosting through Netlify
- To solve the website problem, it is good to inspect the website using Chrome or Firefox
- Using live coding to see live fixes and apply them to the local files is handy
- Using the command cmd+shift+r will force a refresh of the website and cache to allow for new changes to occur
- This was taught by Jason as it was frustrating for him and myself to be unable to see direct changes to our website even though the repository on GitHub or GitLab was updated recently
- Embedded a tweet using an iFrame
- Researching about bug bounties platforms and responsible disclosure policies
- Proof reading blog before publishing and submission
- Started the reflection early to reduce amount of compiling time by the end of the week
What problems occurred?
- Unknown styling errors occurred and cause the sub-html pages to lose its theme
- On a mobile or narrow view of the website, the navbar will always be opened and cannot collapse.
- The hosted website site will not update quickly and requires 5-10min for it update. (Fixed by cmd+shift+r)
- What am I going to do?
- Start learning about web penetration skills
- Understand the vulnerabilities of web applications
- Develop a methodology to break in to web applications
- Develop a methodology to mitigate the potential risk of an exploitation
- Use resources such as:
- Natas
- Webgoat
- HackTheBox
- MrRobot CTF
- Bug Bounty Platofmrs and Responsible Disclosure Policies Homework due on Wednesday
What did we do on Wednesday?
What have I learnt?
Fixed my website
- Asked help from Darsh and Vishal for another opinion tackling a problem
- Navbar error
- Bootstrap collapsing a navbar would override state of it and leave it open regardless if the Boolean was true or false
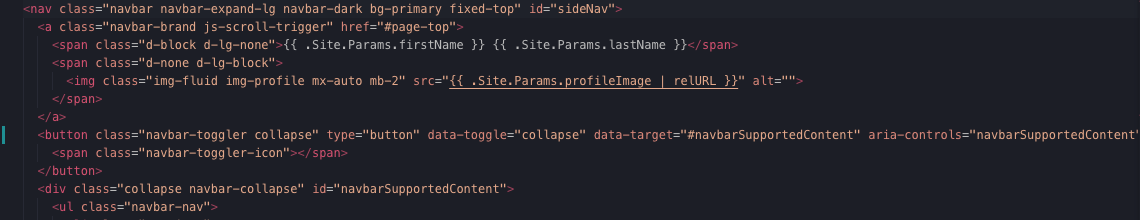 Screenshot of my code in Visual Studio code of the problem.
Screenshot of my code in Visual Studio code of the problem.
- This problem was fixed by shifting the order of one of the classes and Boolean statements. It is not quite clear which code caused the error as it fixed itself and I was unable to re-code the error.
- Theme error with linking path of resume.css and tweaks.css to the baseurl
- Changing the baseof.html
- Redirecting the error from ‘css/resume.css’ -> ‘../../../css/resume.css’
- Redirecting the error from ‘css/tweaks.css’ -> ‘../../../css/tweaks.css’
- The biggest challenge I got out this was that the normal css/resume.css directory would not work on the hosted domain but would work on the local host.
- This was solved through the help of Vishal and his knowledge to live edit the code using chrome.
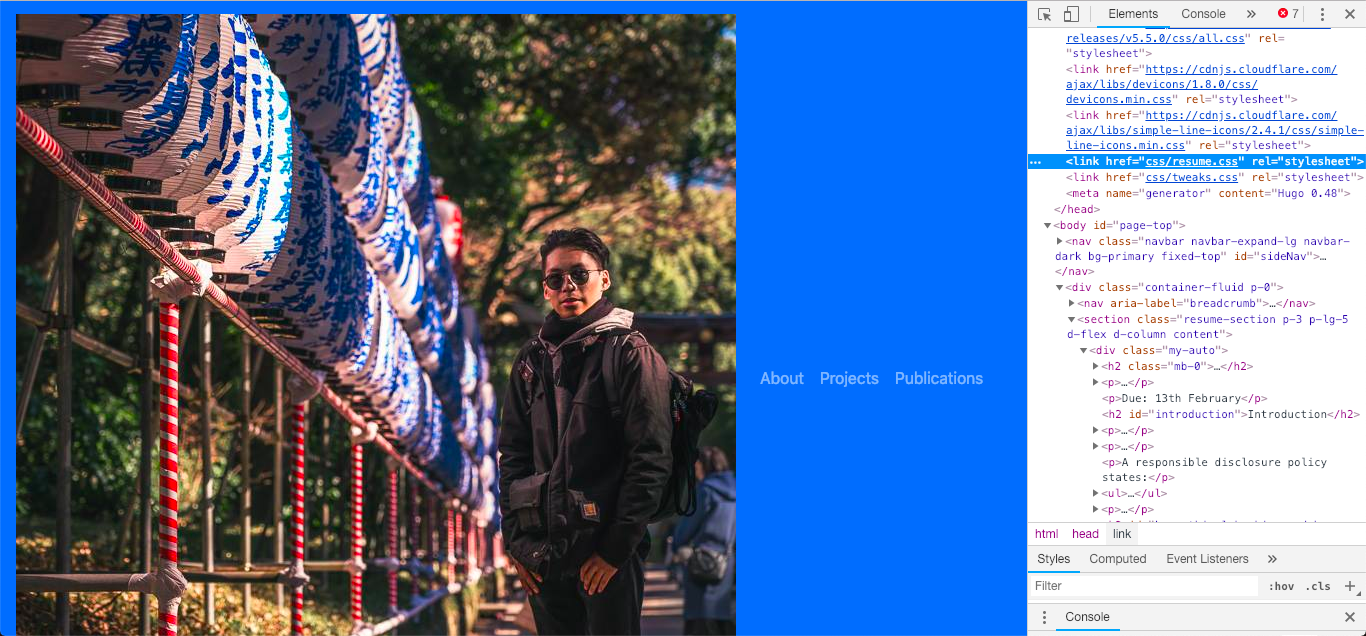 Screenshot of inspect feature and that full screen yields a big problem with the css.
Screenshot of inspect feature and that full screen yields a big problem with the css.
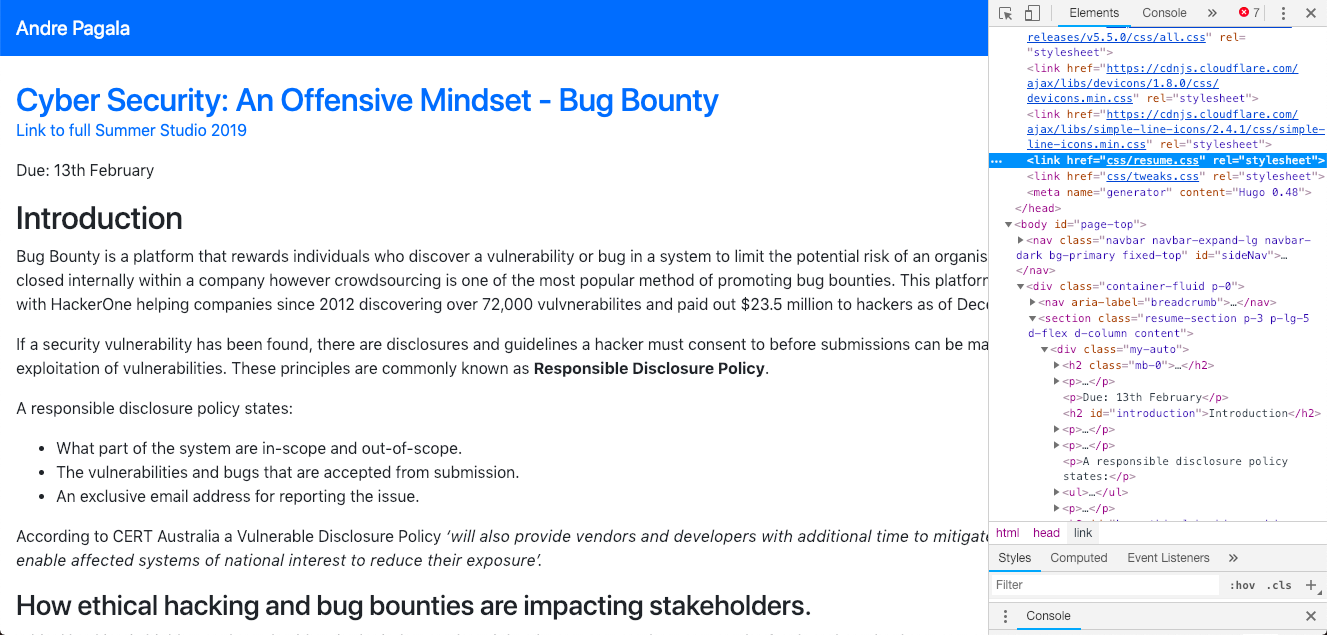 Screenshot of the same problem but the navbar is in mobile mode and the css is still broken.
Screenshot of the same problem but the navbar is in mobile mode and the css is still broken.
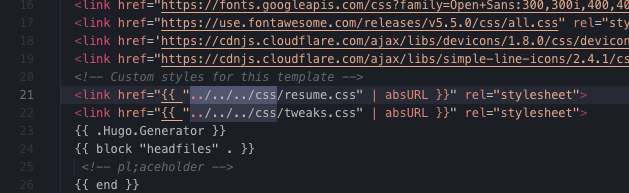 Screenshot of my code in Visual Studio Code of the problem fixed.
Screenshot of my code in Visual Studio Code of the problem fixed.
- XSS
- Reflected
- Stored
- DOM-based
- Finding a real life example
- Artefacts
- A crypto website
- using DOM to inject a gif of Jesus into a ‘#send-payment’ session
 A snippet of Jesus inectjed into the send payment function.
A snippet of Jesus inectjed into the send payment function.
What problems occurred?
- N/A (Most of my problems on the Static Website was Solved)
- A future problem is to fix the design of the website but this is currently out-of-scope.
What am I going to do?
- Develop a problem statement on web-application security.
- Present a real-life problem and example and describes the steps why it has vulnerabilities
What did we do on Friday?
What have I learnt?
- I have developed a problem statement on web-application security - **How do we viably protect our web-applications from attacks in 24⁄7 economy?
- In a global economy where the downtime of any web-application can cause disruption in the profit and its effective usage.
- Compared to the last 10 years of technology and the usage in the online world, cybercrime has a very high potential of taking over the profits of drugs in the next 5 years. Criminals are becoming more technological knowledgeable and using web applications and their vulnerabilities to their advantage.
- Free-for-all Stand Up Meeting
- Paired up with Jason, Rowan and Mitchell, I have learnt that everyone is currently having time with time management and it apparent through the lack of sleep. However, everyone has been giving their best by providing interesting facts about web security application and what they are struggling with.
What problems occurred?
- Punctuality
- I have arrived late to class by 10 minutes and the tutor has formally told us that if we are more than 15 minutes to class it will be a misconduct that will have to followed up with UTS.
- Presented our problem statement on web-application
- I should have created a PowerPoint presentation to summarise my blog about web application security as it was dense information. By using slides, I can better time myself and make use of the given time effectively as I was unsuccessfully unable to finish. Prior to the presentation, I want to experiment if I could talk without the use of physical artefacts such as slides or notes in my hand to trigger my memory. However, this led to my speech to be slurred throughout as I was panicking to get to end before time was up.
What am I going to do?
- Punctuality
- Catch the earlier train so I can get to university at least 30 minutes before class starts so I can become focus as soon as it starts.
- Improving technical skills
- I am going to keep pushing myself by doing write-ups of the web application challenges I have done so far and hopefully sign up to the CTFs and pentesting websites like HackTheBox and MrRobotCTF.
OVERALL SPRINT
Friday Presentation
I have done a lot of research of web application security how a hacker can use simple vulnerabilities from google search and can exploit them and install malwares which potentially can encrypt any file they wish in exchange of a untraceable payment. This research can be read through this link about web application security.
Natas
This is not my first time of trying to break into web application security by this will be first completing a write-up hopefully up to level 15. Write-ups are great method to understand and validate your solutions. It’s great way to build a bank of knowledge to build of up the knowledge to quickly recognise vulnerabilities. This write up can be read by clicking this link about natas.
Bandit
Currently in progress.
Evaluation
For the last couple of years, time management hasn’t been a major problem however this studio has shown me how important it is to be diligent and discipline in following a schedule. Everyone has their own personal life with family, work and school, so that means we all make compromises to meet to deadlines and expectations.
This week I handled things differently and viewed it from it another perspective. Compared to last week where I was perceiving the task as a whole, this week I cut the task into manageable sections that I can complete over the scheduled days. This approach was great for myself as I did not get too overwhelmed with completing the homework and extra web application technical practice during my own time. I also found that it was much more effective of trying to put key points into statement rather than trying to bolster it up with security jargon.
I believe for me to get the most out of this subject is that not be the top of the class however at the technical skills and high language level I can reciprocate what I have learnt during this time to those who did not have the opportunity to enrol in this studio.
In comparison to last week, my health has really took a toll by unable to get a good quality of sleep and enough food to eat. I tend to sell myself short by misleading myself that I am not up to everyone’s skill level in technically and knowledge and that I need to push myself further to catch up. Since I can become very meticulous and a bit of perfectionist this does not make my situation any better. To fix tiring out my mental capacity, I have to take frequent breaks and review what I need to complete in the next hour before my next break so I can slowly develop a better method of studying.
Expectation
Next week will be the big challenge for everyone and especially myself. This will be the next step in reaching my goal of working in the cyber security industry. Although I may not have the expertise I desire, I know I have developed a good design thinking methodology which I can use to slowly progress myself throughout the week.
The last two weeks the tutors have been quite lenient on us and I believe week they should start become a bit more strict. Taking advantages of their leniency I can quickly fall back into a path where I can become complacent and unmotivated to do better. However, I do appreciate the level of transparency they have provided through the last two weeks every day. I am lucky to be enrolled in this subject as it is not often that tutors will go out of their way to help myself find where I am currently and if I need any help to guide me. If the tutors keep giving their 110% each day we cannot disappoint them by not putting in our own effort as well. At the end of the day, it is a subject of self-learning.
CONCLUSION
Every week has been increasingly becoming more challenging and invigorating. The habit to create and to follow a timeline has been very difficult for me validated by staying up late trying to improve myself every day to put in the 35hrs of effort. However, this is stepping stone for myself to lead to create and achieve bigger goals if I keep working on it during my own time. By giving it my best every week, my struggles will yield positive outcomes.
BIBLIOGRAPHY
Using UTS Harvard Referencing.
OWASP 2017, ‘Types of Cross-Site Scripting’, OWASP, viewed 17 February 2019, https://www.owasp.org/index.php/Types_of_Cross-Site_Scripting UTS 2018, ‘Interactive Harvard UTS Referencing Guide’, UTS, viewed 17 February 2019, http://www.lib.uts.edu.au/sites/default/files/attachments/page/InteractiveHarvardUTSGuide.pdf OverTheWire n.d, ‘Natas’, OverTheWire, viewed 17 February 2019, http://overthewire.org/wargames/natas WebAppSec 2005, ‘DOM Based Cross Site Scripting or XSS of the Third Kind, Amit Klein, viewed 17 February 2019, http://www.webappsec.org/projects/articles/071105.shtml GitHub 2017, ‘Markdown Cheatsheet’, Adam P, viewed 17 February 2019, https://github.com/adam-p/markdown-here/wiki/Markdown-Cheatsheet Github 2012, ‘What’s the difference between a web site and a web application? [closed] ‘, Prusrus, viewed 17 February 2019, https://stackoverflow.com/questions/8694922/whats-the-difference-between-a-web-site-and-a-web-application