Cyber Security: Offensive Mindset - Sprint 3
Timeline: 18th - 24th
Due: 24th February 11pm
INTRODUCTION
This was an extremely challenging week for everyone and especially for myself. This week was about applying our knowledge for the past 2 weeks and to try for ourselves to crack boxes. These boxes mainly revolve web penetrations where students will have to demonstrate their capabilities using the tools they have found and learnt to gain root access. Root is access is classified as the highest level of privilege a user can gain. This means a user can run any command or application they want.
An overview of the week includes:
- Monday
- Darsh’s demo of his box trying gain root privilege through WordPress vulnerabilities,
- Wednesday
- Deloitte’s representatives explored through what a red team member does
- A practice box
- Group presentation on penetration tools
- Friday
- UTS Security Analyst Intern Interview
- Demonstration by Jai on Deloitte’s box
To prevent myself from losing track of what tasks I needed to complete, I made a Kanban board. The screenshot below shows an overview of sprint 3.
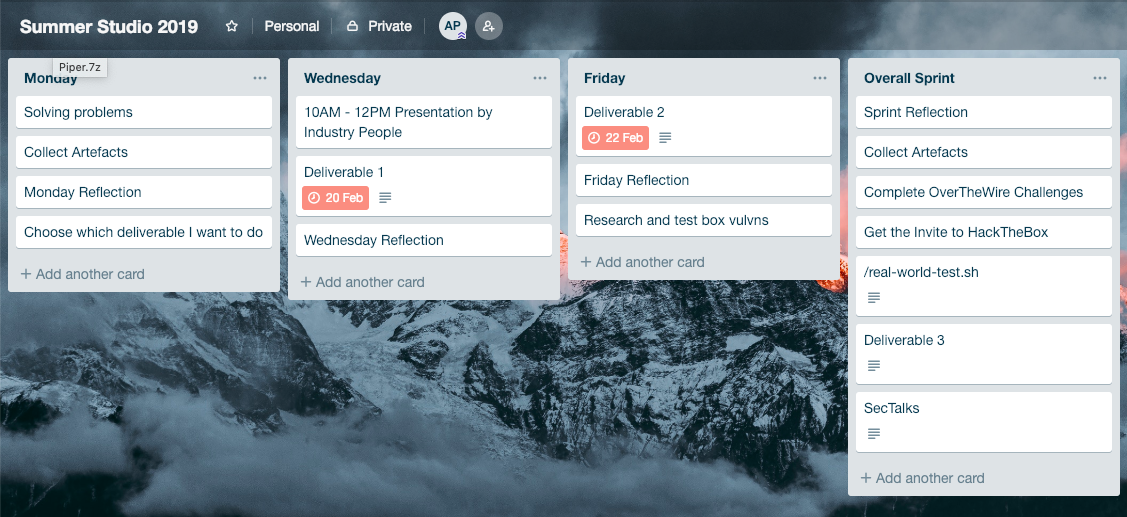 Screenshot of Trello Kanban Board of Sprint 3
Screenshot of Trello Kanban Board of Sprint 3
IN-CLASS
Monday
What have I learnt? (Learning)
- Learnt about the different type of boxes we can crack
What problems occured? (Challenges)
- Doing a Kanban Board using Trello to clarify my tasks due on a daily basis.
- Made a group on Monday to presents security tools CyberChef and Wireshark.
What am I going to do? (Solutions)
- Networking
Wednesday
What have I learnt?
- Subnetting
- CyberChef
- Open source swiss-army knife with mulitple functions including cryptographic, compression and hashing operations.
- Under active development, new functionality added with each update
- Online web app and also desktop based
- Support drag and drop for files up to 500MB and supports breakpoints in the browser
- Can chain series of operations (recipes) together to transfer data
- Extremely useful when you’re confronted by different type of encryptions and don’t know where to start
- It’s free to use online and offline
- Uses operations that can use simple to complex encryption or decryption
- Simple Operation
- XOR or Base64
- Complex Operation
- AES, hexdumps, hashes, checksums or character encoding
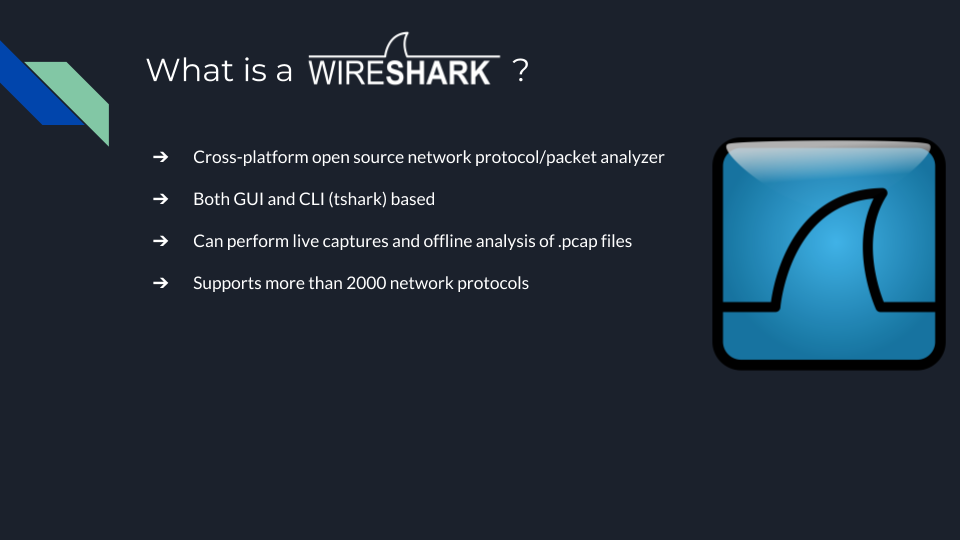
- WireShark
- Cross-platform open source network protocol/packet analyzer
- Both GUI and CLI (tshark) based
- Can perform live captures and offline analysis of .pcap files
- Supports more than 2000 networks protocols
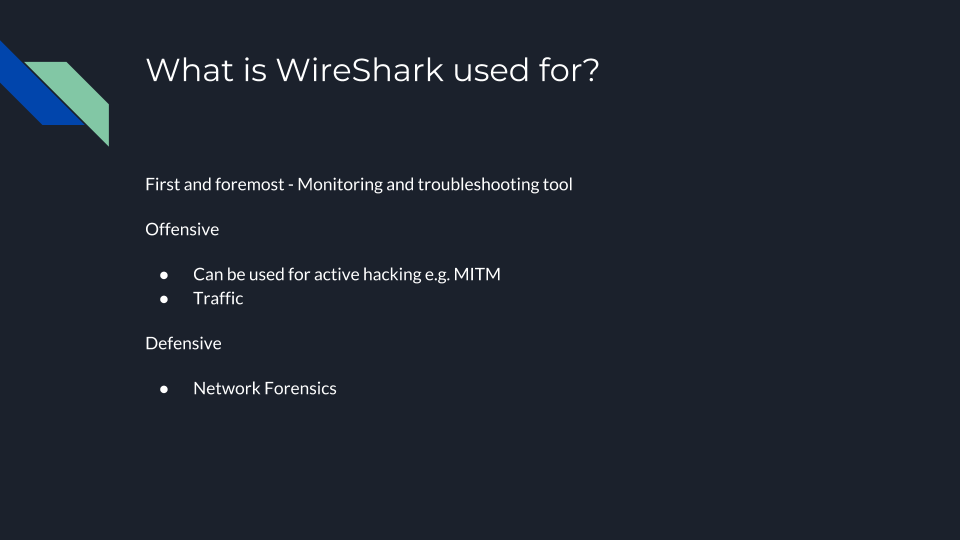
- Monitoring and troubleshooting tools
- Offensive
- Active hacking e.g. MITM
- Traffic Analyzing
- Defensive
- Network forensics
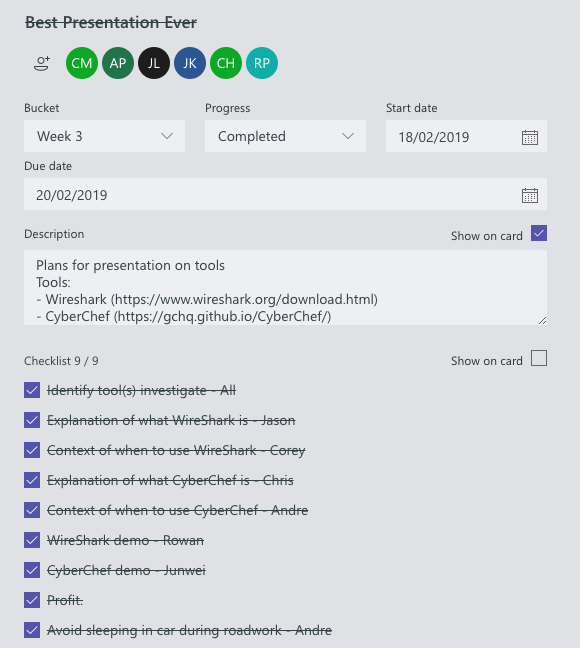
- Group Presentation Preparing
 |
 |
|---|---|
 |
 |
 |
- Bare Minimum Bandits Presentation Slides
 |
 |
|---|---|
 |
 |
Screenshot of my slide in the group presentation
What problems occured?
Complex subnetting got really confusing one you had mulitple networks and variable hosts amounts.
What am I going to do?
- Complete Mr Robot CTF
- Networking
- OSI
- TCP/UDP
Friday
Free-for-all
- I talked with Mitchell Tuck and explain what went wrong today with my interview.
- An example what went wrong was figuring out how many networks are in /24.
- I said 128 but the correct answer should 256 hosts and 258 submasks.
- My reasoning for 128 was that it was the biggest binary number of the octet but I forgot to all the rest of 7 bits. 128 + 64 + 32 + 16 + 8 + 4 + 2 + 1 = 256. 256 - 2 (broadcasting and receiving) = 254. 0.0.0.0-255⁄24 with an increment of 1 bit. E.g. 0.0.0.1, 0.0.0.2, 0.0.0.3, … and 0.0.0.255. However 1-254 are the only usable hosts.
- Mitchell had a go with the Deloitte box however hit a couple of roadblocks on the way. He was successful getting the username and password to the site however didn’t have enough experience with deploying a reverse shell.
- Mitchell tried few reverse shell he found on google but none on them work. I suggest he should try finding reverse shell in python.
- He also had problems with getting his Kali to work as it’s unable to be turned on in the VMWare software.
What have I learnt?
- Networking
- TCP/IP
- OSI
- Layer 1 - Physical
- Layer 2 - Data Link
- Layer 3 - Network
- Layer 4 - Transport
- Layer 5 - Session
- Layer 6 - Presentation
- Layer 7 - Application8
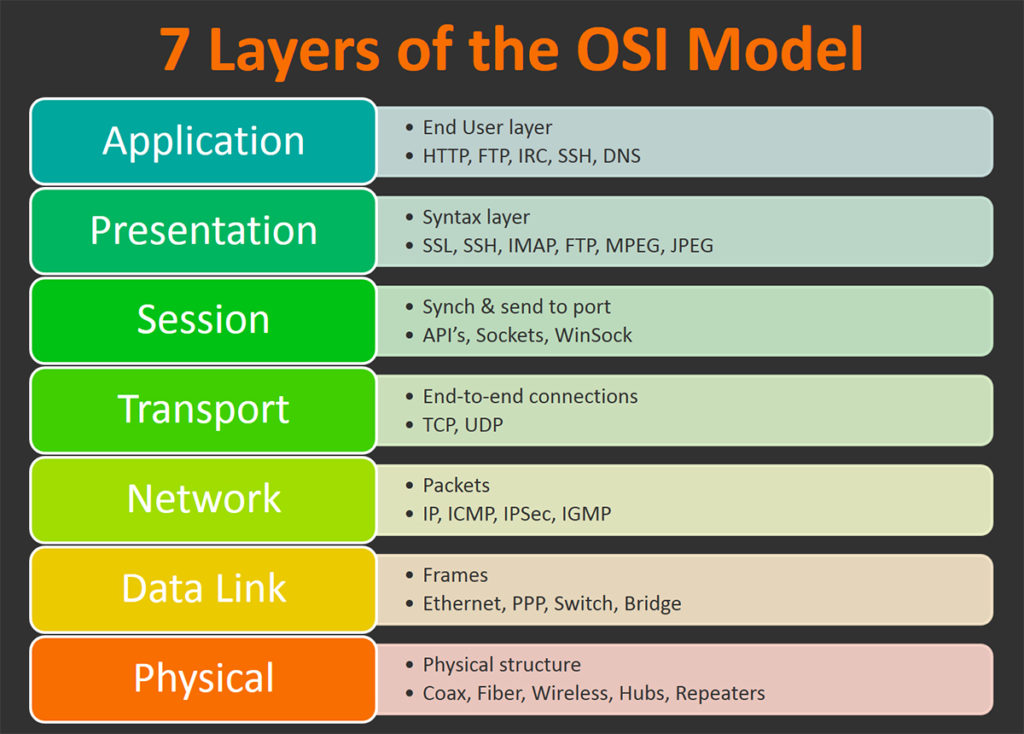
OSI model from BMC blogs
- Subnetting
- Binary to decimal equivalent
- Calculating host address
- Calculating network address
- Calculating submask address range
- SSL/TSL/HTTPS
- Common ports
- 443 - HTTPS
- Web Pentesting
- Wordpress Vulnerabilites
- Wpscan
- Metasploit
- Exploit DB
- Hydra
- Burp Suite
- John the Ripper
- Hashcat
- Cyberchef
- TryHackMe - Mr Robot CTF
- Learning how to enumerate through problems
- Burp Suite to find credentials
- Hydra
- Wpscan
What problems occured?
- The interview didn’t go as expected even though I study the basic networking terminologies. I believe that I became too anxious thus doubted my answers causing them to be wrong.
- Mr Robot was fun to learn as it was first proper time cracking a box.
What am I going to do?
- Cracking Deloitte’s box
- Complete my sprint 3 reflection
OVERALL SPRINT
UTS Security Analyst Intern Interview
By trade, I am a software engineering student however this does not stop me from learning outside of my technical field. This is proven enrolling in this subject and joining the Cyber Security Team. The downside of not studying a security related degree, I have very basic networking knowledge that I can use. The extent of my understanding is setting up simple port forwarding servers for games like Minecraft, routine maintenance on all devices updating software firmware, changing default credentials and assigning static IPs to desktop systems.
I had to learn basic networking from scratch however I had no clue where to start. I asked help from the tutors and friends who have completed network subjects what are the important aspects of networking I should start with. A good start with networking was learning the OSI model and subnetting.
 |
 |
|---|---|
 |
 |
 |
 |
 |
 |
Web Penetration
This week was intense with the amount of self application to gain root access to the boxes that were demonstrated throughout this week.
SecTalks
SecTalks is a monthly seminar that is at PWC hosted by the real world industry security professionals. This week’s workshop was about Zigbee and 802 protocol.
Zigbee is an IEEE 802.15.4 high level communication protocol used to create small network with IoT devices. This talks revolved around using a Zigbee to receive packets. It is important to note it is illegal to transmit using a Zigbee without permission by the owner of the network it is scanning.
The zigbee was used to scan for packets that were openly transmitted over the zigbee protocol which accumulated a lot of a data in raw format. They proceded to convert the raw file in a pcap file that allows tools like WireShark to analyse that data was being transmitted to be destined to be received.
Evaluation
Prioritisation is difficult to manage when you have to many tasks to complete. Whether they may require alot of time to minimal amounts, the quantity of tasks to complete can be overwhelming. I expected to able to solve a minimum of 2 boxes however I was only able to solve Mr Robot CTF.
Expectation
I hope next week I can fully devote 100% of my time and effort to continually hack more boxes including completing challenges in HackTheBox. As a software engineer, this next week will be intriging as I will be able to put some of my programming knowledge into reverse engineering web applications or anything our guest speaker will challenge us with.
CONCLUSION
This week as expected was the most challenging week yet due to having a limited amount of time to work on boxes and learn IT networking. I have developed a good basic understanding of networking which included subnetting calculating what submask address are allocated to a network or host, TCP/UDP ports and many more networking topics.
Bibliography
Zigbee 2019, ‘What is zigbee?’, Zigbee, viewed 24th February, https://www.zigbee.org/what-is-zigbee/
Wikipedia n.d., ‘OSI Model’, Wikipedia, viewed 24th February, https://en.wikipedia.org/wiki/OSI_model
BMC n.d., ‘OSI Model 7 layers’, BMC, viewed 24th February, https://www.bmc.com/blogs/osi-model-7-layers/
Microsoft n.d., ‘Windows network architecture and the OSI model’, Microsoft, viewed 24th February, https://docs.microsoft.com/en-us/windows-hardware/drivers/network/windows-network-architecture-and-the-osi-model
Network World n.d., ‘The OSI model explained how to understand and remember the 7 layer network’, Network World, viewed 24th February, https://www.networkworld.com/article/3239677/lan-wan/the-osi-model-explained-how-to-understand-and-remember-the-7-layer-network-model.html
Cloudflare n.d., ‘Open systems interconnection model OSI’, Cloudflare, viewed on 24th February, https://www.cloudflare.com/learning/ddos/glossary/open-systems-interconnection-model-osi/
Geeks for Geeks n.d., ‘Layers OSI model’,Geeks for Geeks, viewed 24th February, https://www.geeksforgeeks.org/layers-osi-model/