Cyber Security: Offensive Mindset - Reverse Engineering and Exploitation
INTRODUCTION
Today’s 10-12pm class welcomes a cyber security professional works at Symantec. Ruben has been in the security field for the last 4 years of his career with a background of software engineering.
You can find Ruben on Twitter.
His workshop dives into the world of reverse engineering by using binary ninja to find flags for a mini-CTF. Mostly new to this field of security, it was great experience to have Ruben to guide us through this endeavour.
REQUIRED TOOLS
Reversing engineering and exploitation tools come in all shapes and sizes meaning you don’t have to use tools listed below (lightweight version of open source software is preferred if available). Like everything in this subject, there is no right way to complete a task; there are always multiple solutions to a problem. You can choose any tools you’re comfortable with.
Other mentionable tools like IDA PRO have been suggested as a preferred reverse engineering software however acquiring a license can be expensive for an individual especially if you’re a student.'
Binary Ninja

Binary Ninja is a reverse engineering platform that provide developers and security professionals disassembly code formatted for human-readability.
The demo version of binary Binary Ninka is free to demonstrate basic functionality for the requirement of this workshop. It is available platform: OS X, Linux and Windows.
GDB

GDB is a debugger that allows you see the instruction of a inside another program while its running. It is particularly helpful to diagnose the moment another program when it crashes.
If your GDB is outdated you can download the most recent official release of GDB.
Important issue to note for OS X users, there is no official support for GDB on OS X however it can work to an entext. From experience, downloading the latest version of GDB on my mac resulted in unable to locate the file to be debugged. I have tried multiple method from Stackoverflow and other sources but none have been successful. Highly suggest use Kali as it already has GDB installed.
PEDA - Python Exploit Development Assistance for GDB
PEDA enhances the user usability of GDB by displaying disassembly codes with logical colorize texts, registers and memory information during debugging.
Extra Commands to support debugging and exploit development. Without this you will be unable to debug through GDB. Other alternatives that is similar to PEDA is GEF.
 Screenshot from the GitHub page of PEDA's command
Screenshot from the GitHub page of PEDA's command
Challenges
0x01 Abradolf Lincler

Although I have seen people using Binary Ninja to solve flags for CTFs and during SecTalks, it was my first time ever using binary ninja indepth. I have no clue how it works and what I am suppose to be looking for. Intimated by the shear scale of it’s functionality, I simplified the program by using my software background.
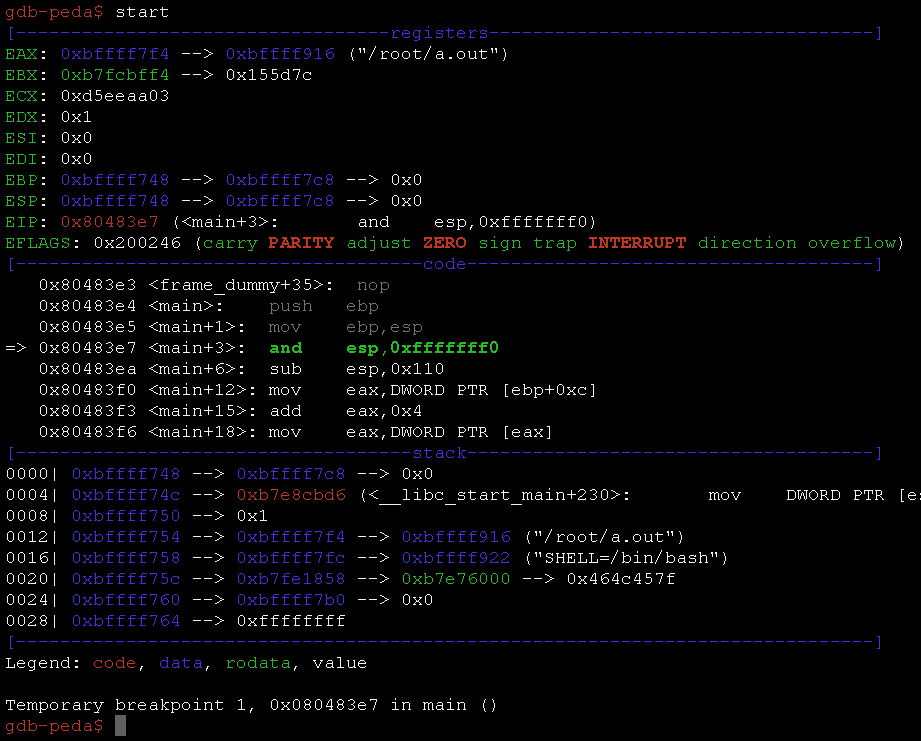
 Running the binary is first step to figure out what the program the actually do.
Running the binary is first step to figure out what the program the actually do.
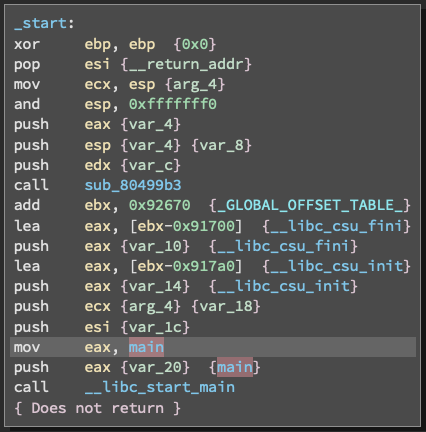 Opening the file into Binary Ninja launches into this interface. This screen describes the steps and functionality what the program is executing when it starts. Using basically software programming knowledge of C or C++ we know that the programming will transition in to a 'main' method, noted by 'mov eax, main'.
Opening the file into Binary Ninja launches into this interface. This screen describes the steps and functionality what the program is executing when it starts. Using basically software programming knowledge of C or C++ we know that the programming will transition in to a 'main' method, noted by 'mov eax, main'.
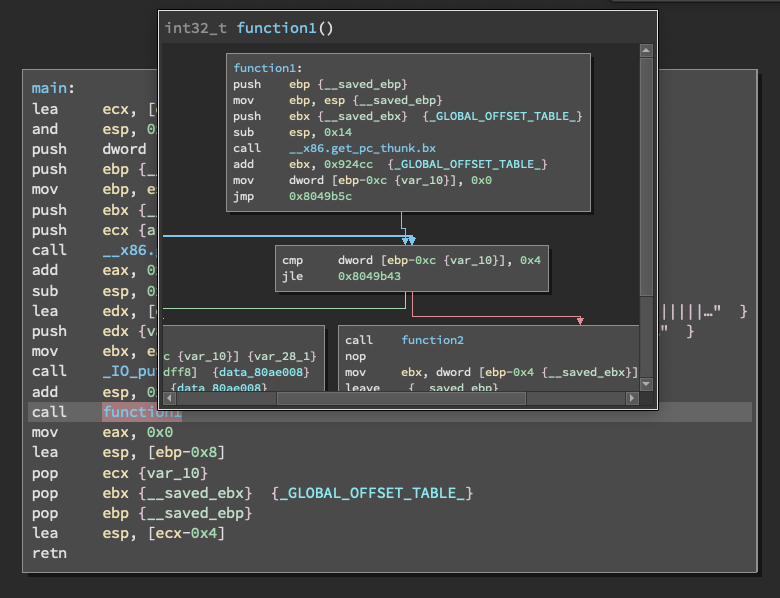 The most important aspect of basic programming is that your main function will execute methods in a class. This is shown through the 'call' function that executes 'function1'.
The most important aspect of basic programming is that your main function will execute methods in a class. This is shown through the 'call' function that executes 'function1'.
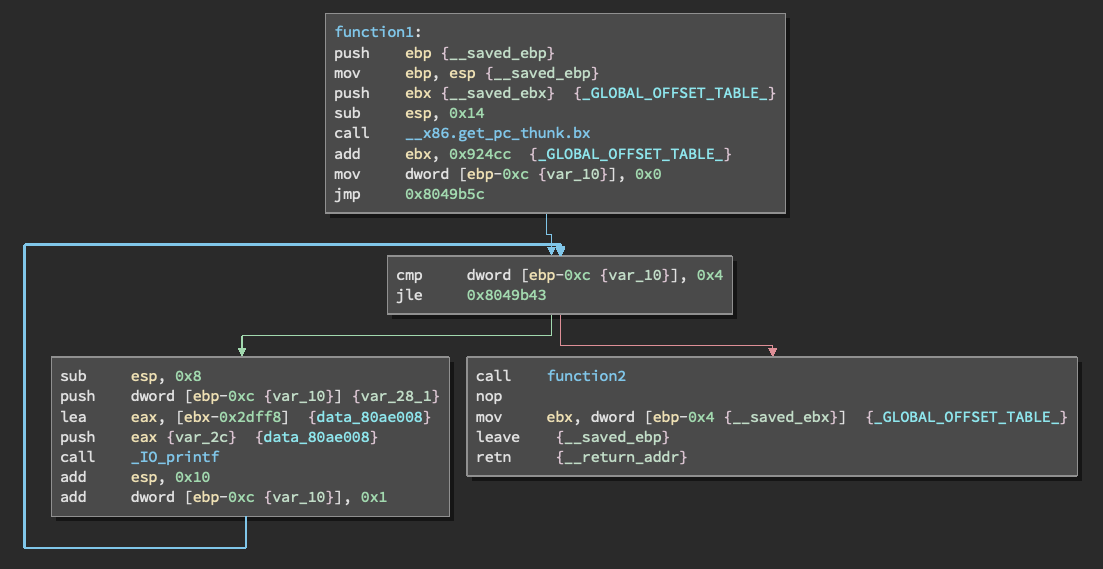 Noting from function1, its describes the statement of a loop and if else statement detouring to 'call function2'. According to the loop, it will cycle 4 times before calling function2.
Noting from function1, its describes the statement of a loop and if else statement detouring to 'call function2'. According to the loop, it will cycle 4 times before calling function2.
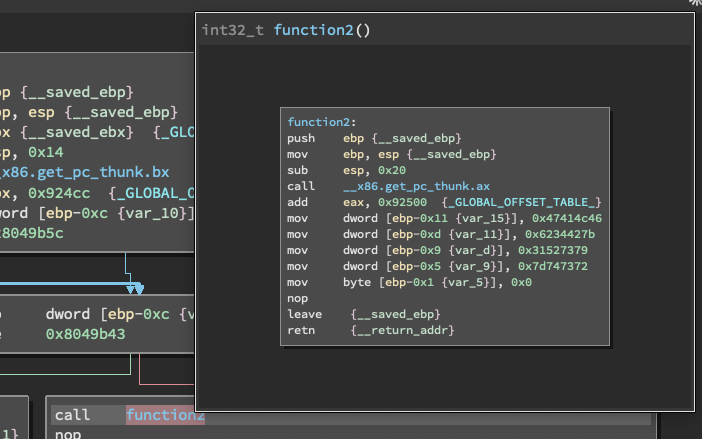 Hovering the cursor above the method allows us to preview the function without entering the graph interface of it.
Hovering the cursor above the method allows us to preview the function without entering the graph interface of it.
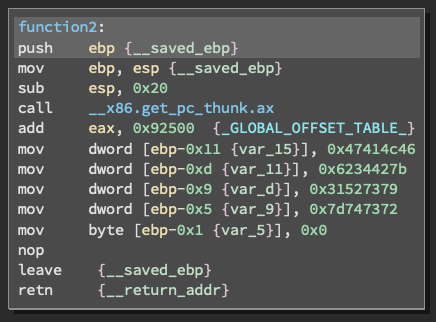 At this point I was quite stuff how to decipher the raw values, however Ruben gave clues that you can change the values to another data set within Binary Ninka. It was becoming increasingly clear that we were on the right path judging that only 4 values where passed through and ended with a 0x0 statement to stop the machine from executing any more code.
At this point I was quite stuff how to decipher the raw values, however Ruben gave clues that you can change the values to another data set within Binary Ninka. It was becoming increasingly clear that we were on the right path judging that only 4 values where passed through and ended with a 0x0 statement to stop the machine from executing any more code.
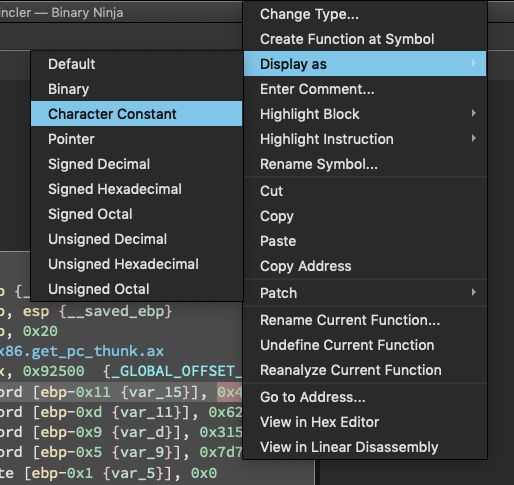 Within Binary Ninja, you can change the default values to 'Display as' a 'Character Constant'. This image below will reveal the flag of this first callenge.
Within Binary Ninja, you can change the default values to 'Display as' a 'Character Constant'. This image below will reveal the flag of this first callenge.
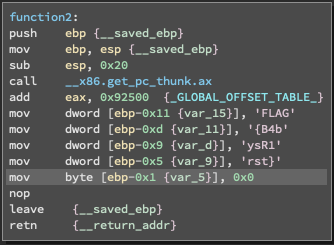 Nice. We have finally reached the end of reversing engineering challnege 0x01 and now it's time submit the flag for those points.
Nice. We have finally reached the end of reversing engineering challnege 0x01 and now it's time submit the flag for those points.
At the end of this lesson, Ruben demonstrated that this workshop is a great way to enter the world of reverse engineering by putting yourself straight into a challenge.
Only by doing the most basic levels of reverse engineering challenges out there I was able to learn how to Binary Ninja and GDB intuiatively.
0x02 Morty Crypto
Using our previous knowledge, I digged into the function like the previous question trying to find string function.
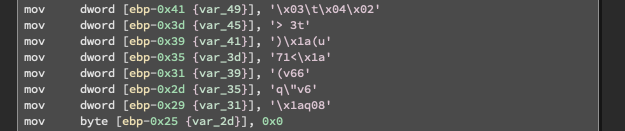 Everyone saw the 0x0 and assumed it was a readable string. It was not.
Everyone saw the 0x0 and assumed it was a readable string. It was not.
Converting the values into string character revealed it was unreadable and of course it would be encrypted. This is why security works by converting a value into a unreadable string until it can be decrypted using a key. Learning later on about different type of keys requirement a public key and/ or private, were hinted that this function uses a key.
Something looked a bit different from the last challenge in the loop method in this main function. XOR.
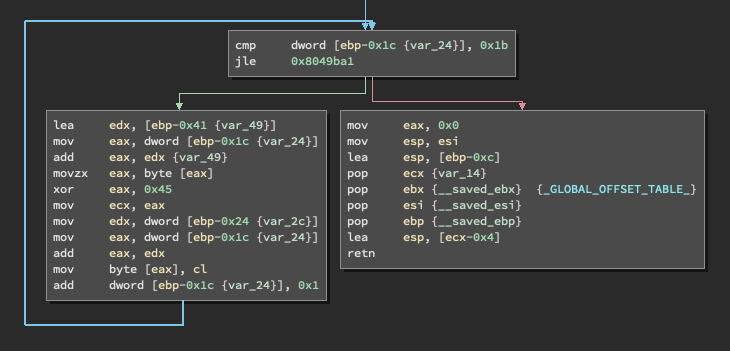 Screenshot of using binary ninja to figure out how it worked.
Screenshot of using binary ninja to figure out how it worked.
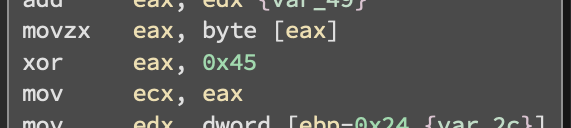 XOR Function containing the key '0x45'
XOR Function containing the key '0x45'
So, what do we now? We can blindly go into GDB, run the program, create breakpoints and assess what’s being currently ran. Otherwise we figure out what happens within the loop function before input commands into gbd.
Firstly, it is always a good idea to run the program and analyse the output. It could provide us with hints or nothing.
Important note before starting to create breakpoints is to install peda or gef. Both of these are assistance tool for gdb to reverse engineer the program.
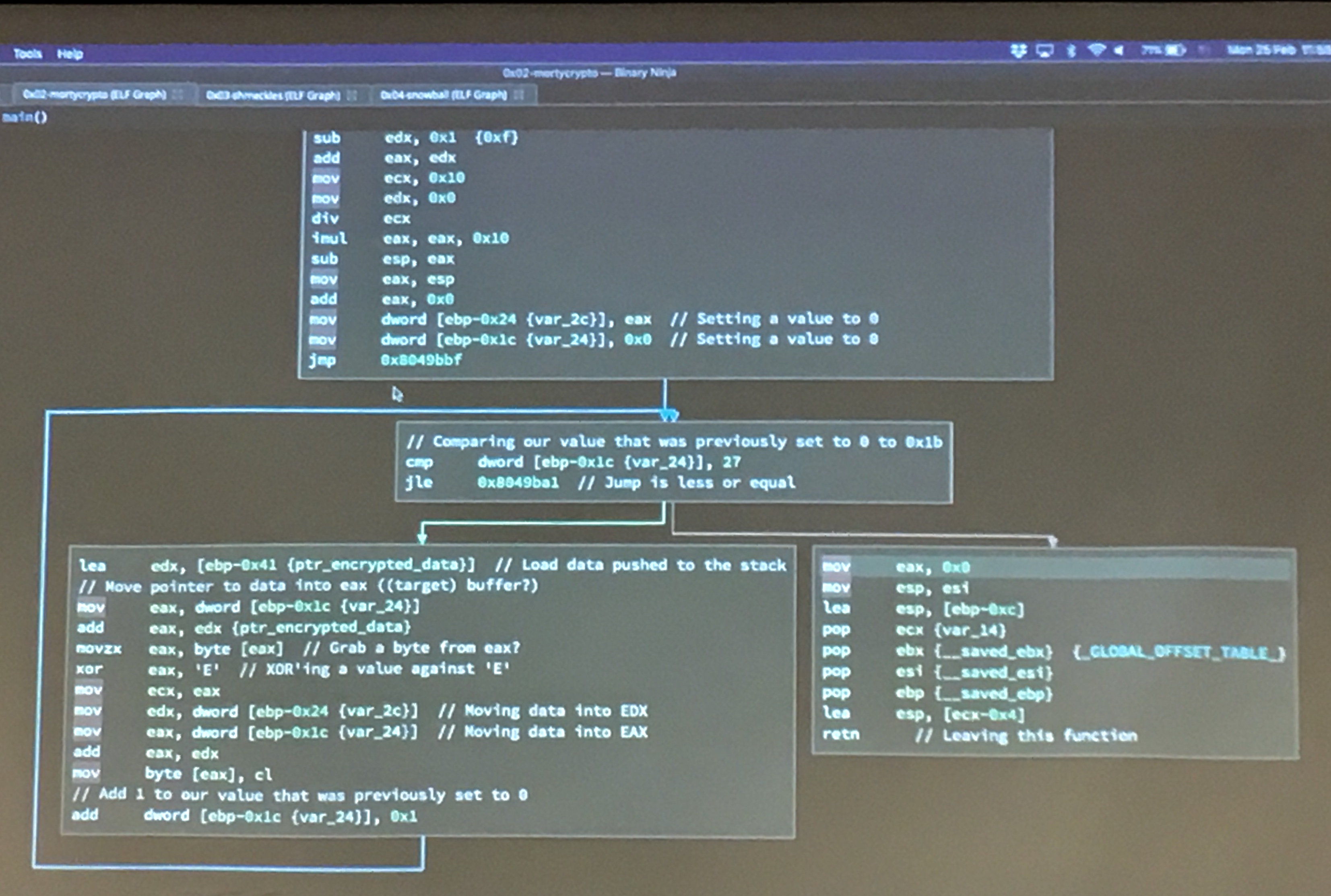 A photo taken during Ruben's live demonstration showing how it enumerates through reverse engineering this particular piece of software.
A photo taken during Ruben's live demonstration showing how it enumerates through reverse engineering this particular piece of software.
 From previous knowledge of 0x01 challenge, we know that the flag is a string value and must end with 0x0.
From previous knowledge of 0x01 challenge, we know that the flag is a string value and must end with 0x0.
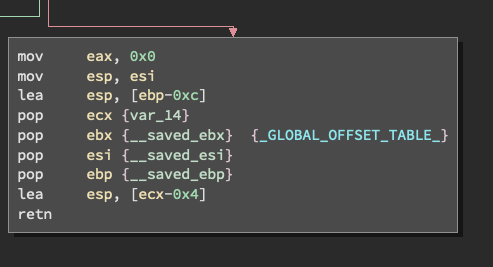
 I wonder what happens if we put a breakpoint at the '0x0' address using GDB. Putting a break point here will lets us further diagnose if what happens when the loop boolean equals true.
I wonder what happens if we put a breakpoint at the '0x0' address using GDB. Putting a break point here will lets us further diagnose if what happens when the loop boolean equals true.
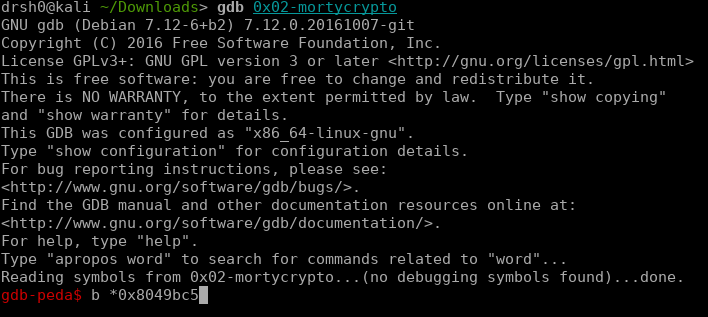 A breakpoint in debugging is considered as an intentional stop to allow the developer to step by step diagnose and anaylze what the code is processing. The debugger will often have interface that shows the user what is line and code is currently being executed as well as store values in variables. To make a breakpoint using a gbd, open bash and type 'gdb 0x02-mortycrypto'. This command will open the 0x02-mortycrypto in the gdb and will look like the image above
A breakpoint in debugging is considered as an intentional stop to allow the developer to step by step diagnose and anaylze what the code is processing. The debugger will often have interface that shows the user what is line and code is currently being executed as well as store values in variables. To make a breakpoint using a gbd, open bash and type 'gdb 0x02-mortycrypto'. This command will open the 0x02-mortycrypto in the gdb and will look like the image above
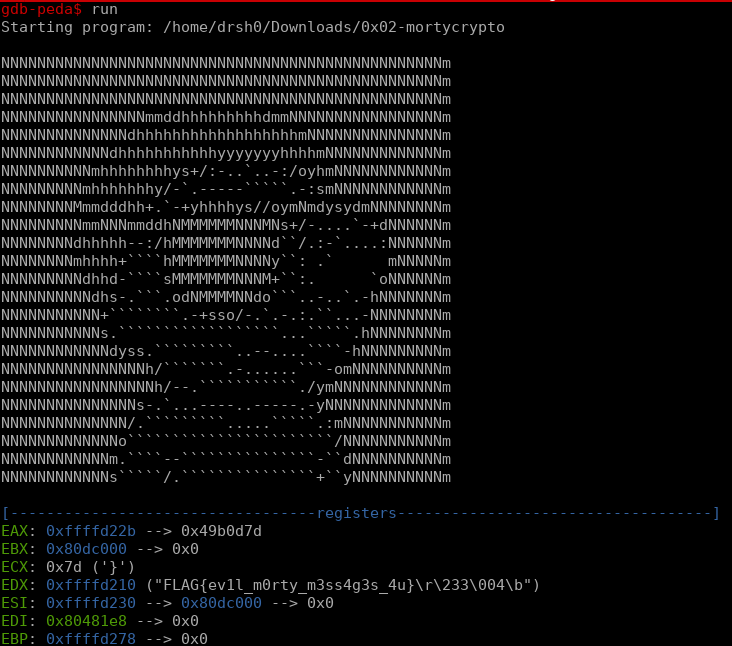 Hey! I think we found the flag. FLAG{ev1l_m0rty_m3ss4g3s_4u
Hey! I think we found the flag. FLAG{ev1l_m0rty_m3ss4g3s_4u
Another way I accidentally found the flag was putting a breakpoint at the XOR function and enter the command ‘n’ for next step. Stepping 100+ steps later, the word FLAG is revealed. By bashing enter, the flag will slowly reveal itself.
0x03 Schmeckles
 In-complete
In-complete
0x04 Snowball
 Not complete
Not complete
CONCLUSION
Undergoing a bachelor in software engineering, this aspect of cyber security was intriguitng and exciting. There was a lot of missing knowledge I thought I had and going straight into Binary Ninja felt like I was programming for the first time except looking at disassembled code.
Currently challenge 0x03 and 0x04 is not a priority until the major portfolio is completed. I would like to dedicate most of time to proof read and finalise my report. However if I complete my porfolio before submission, I would like to complete the remainding challenges and DM Ruben about my results.
BIBLIOGRAPHY
Twitter n.d., ‘RubenthijssenutoutI’, Twitter, viewed n.d., https://twitter.com/rubenthijssen
Hex-Ray n.d., ‘IDA: ab’, Aida6o4, viewed n.d., https://www.hex-rays.com/products/ida/
Binary Ninja n.d., ‘Home’, Binary Ninja, viewed n.d., https://binary.ninja/
GNU n.d., ‘Home’, GNU, viewed n.d., https://www.gnu.org/
Github n.d., ‘PEDA’, longld, viewed n.d., https://github.com/longld/peda
Github n.d., ‘GEF’, hugsy, viewed n.d., https://github.com/hugsy/gef