Cyber Security: Offensive Mindset - Sprint 4
Timeline: 25th Feb - 4th March
Due: 4th March 9am
INTRODUCTION
This is the last sprint out 4 that will conclude the Midas Summer Studio 2019. The week entails the last industry professional talk by Ruben, whom works at Symantec, taught us reversing engineering via a mini-CTF he had created and studio exhibition showcasing our experiences with fellow peers and academic staffs from other studios.
To conclude the subject, the this will be last reflection and there will be multiple deliverables due on 4th of March at 9am. This will include: sprint 4 reflection, vulnerable computer write-up and the studio portfolio.
OVERALL SPRINT
Reverse Engineering
This was introduction to another aspect of reverse engineering of how a computer process machine code by looking at disseembly code. It requires basic understanding of programming how to build a simple program such as executable that prints the words ‘Hello World’.
Just like how a developer can make programs by coding and assemble it in machine code, a hacker can deconstruct assembly code and disassemble it and find how it works.
To help us develop a mindset for reverse engineering,Ruben built his own website to create 4 CTF like challenges. It was extremely fun themed ‘Rick and Morty’ CTF to complete during the 2-hours he was given to present.
To get these flags the following tools where required:
- Binary Ninja
- GBD
- PEDA
Learning to use these tools were extremely confusing to use at first because we didn’t understand the information that was displayed to us. However, through a mini-walkthrough of the software by Ruben it gave us a headstart to find the flags for 2 challenges.
I have made another post that goes into detail about the mini-CTF challenge. Click on the link below. http://pagala.me/publications/studio2019-reverse-engineering/
Friday Presentation
The exhibiton went better than we had expected and it was a fun experience to show our interest of cyber security to fellow peers and academic staff.
Click link below for more detail for about the expo. http://pagala.me/publications/studio2019-exhibition/
HackTheBox
For my vulnerability box submission I will submitting a write-up for Curling. As it is an active box, I will uploading a password protected PDF UTS online and will post the password upon submitting.
However before getting root access to CURLING, to sign-up to the website was a challenge by itself. It required a solid understanding of design thinking of enumerating and pivoting to find clues and put them to together to find a invite code.
Experience finding the code
How to get an invite? Press the link below. https://www.hackthebox.eu/invite
After the last few weeks of going to web penestrating challenges the start of finding any clues was to check the source code by inspecting the websiting using the internet browser. This reveals alots of strange files .
Go to the elements tab and open the script titled /js/inviteapi.min.js.
Looking through this api reveals that this api has many functions including a method to generate a invitation code.
By going to the console tab and type makeInviteCode(), it printed out a message.
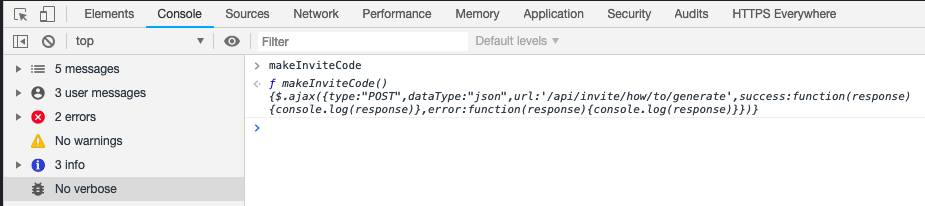 Right click the page to open inspect and go to the console tab to type 'makeInviteCode()'
Right click the page to open inspect and go to the console tab to type 'makeInviteCode()'
This was required to create a html POST using the url ‘api/invite/how/to/generate’.
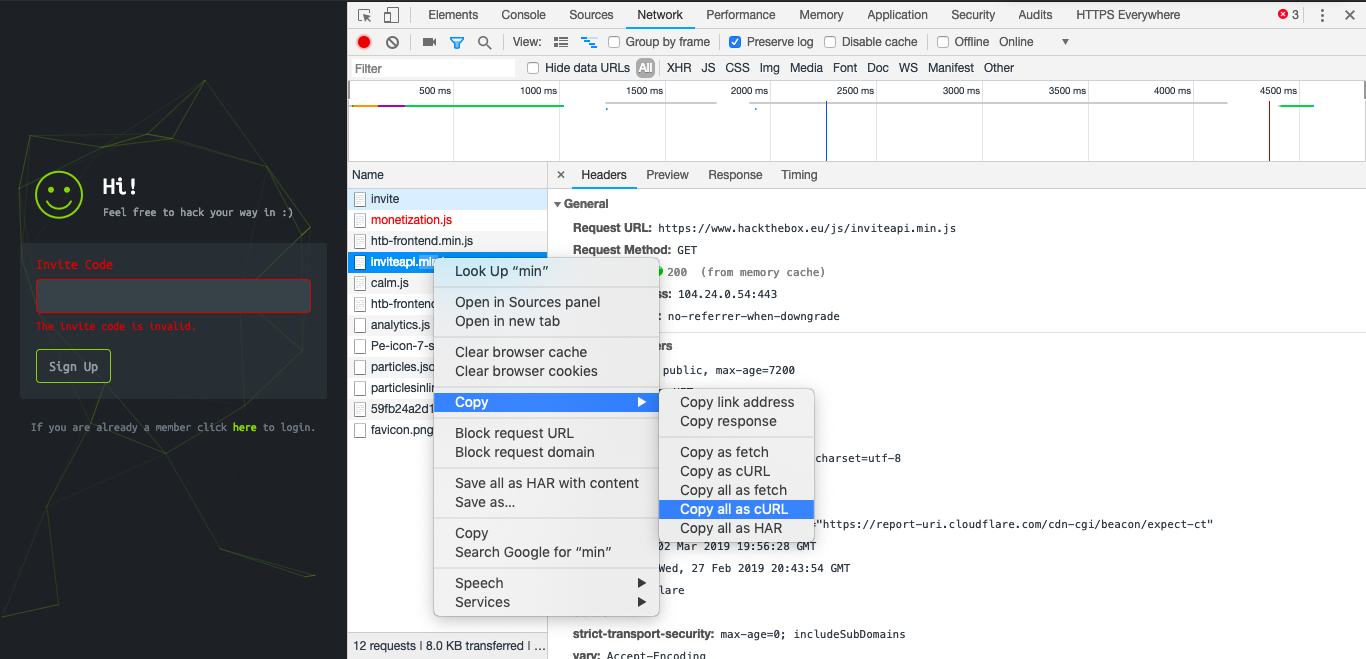 Generating the cURL
Generating the cURL
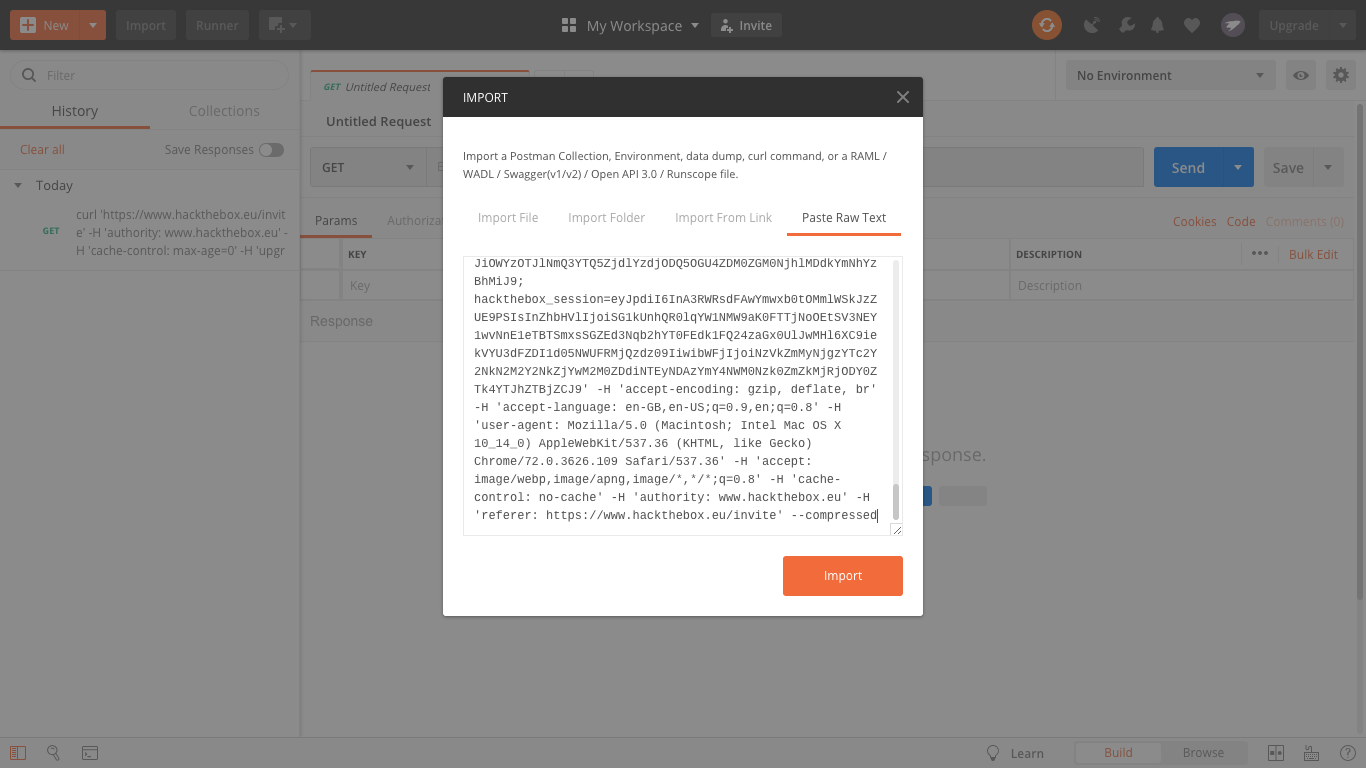 A screenshot of pasting the cURL into Postman.
A screenshot of pasting the cURL into Postman.
I researched how to make a post using google chrome and POSTMAN was recommended tool to easily create posts.
However, the post didn’t work with ‘api/invite/how/to/generate’. So, I thought of shortening it to ‘api/invite/generate’.
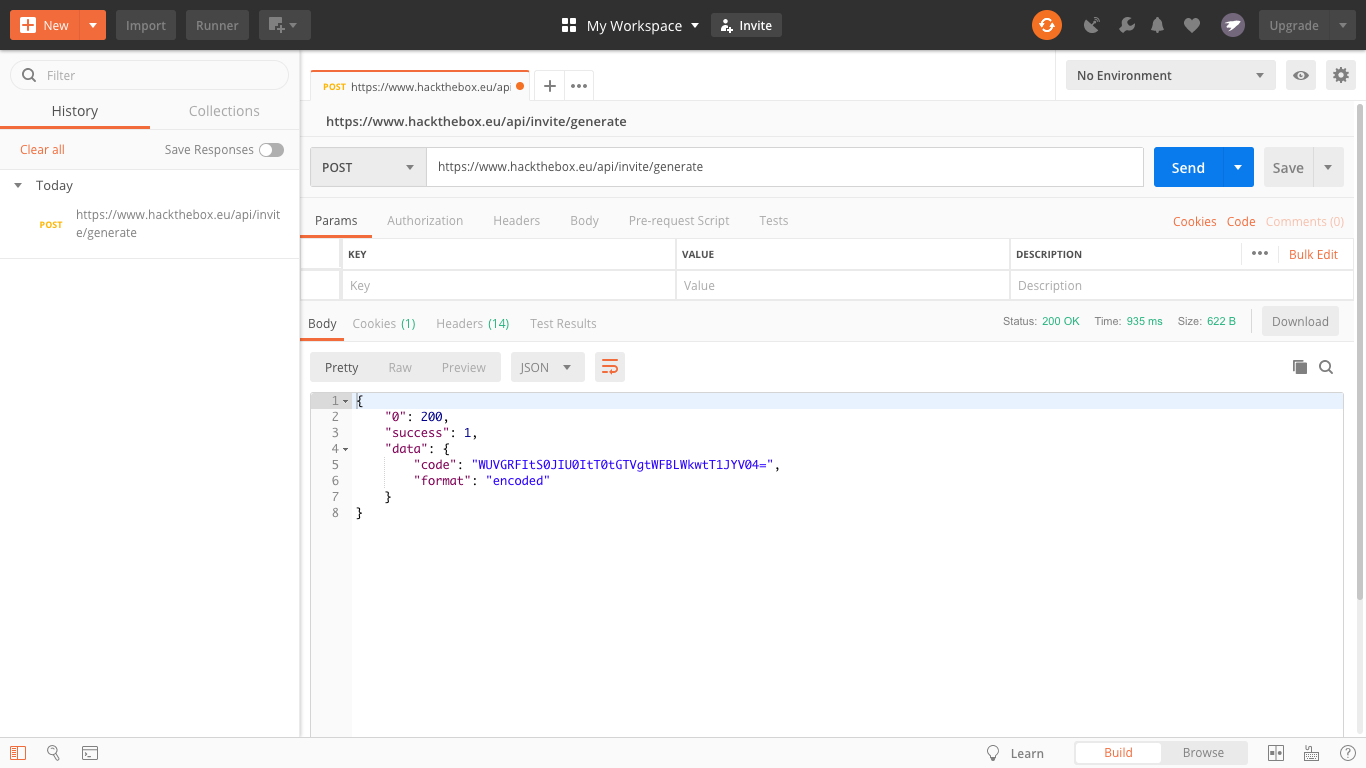 Screenshot of Postman after creating a post using the address 'https://hackthebox.edu/api/invite/generate
Screenshot of Postman after creating a post using the address 'https://hackthebox.edu/api/invite/generate
It looks like a base64 hash based of previous knowledge by identifying the last char ‘=’. I decided to decipher it in using a tool we have previously used called CyberChef.
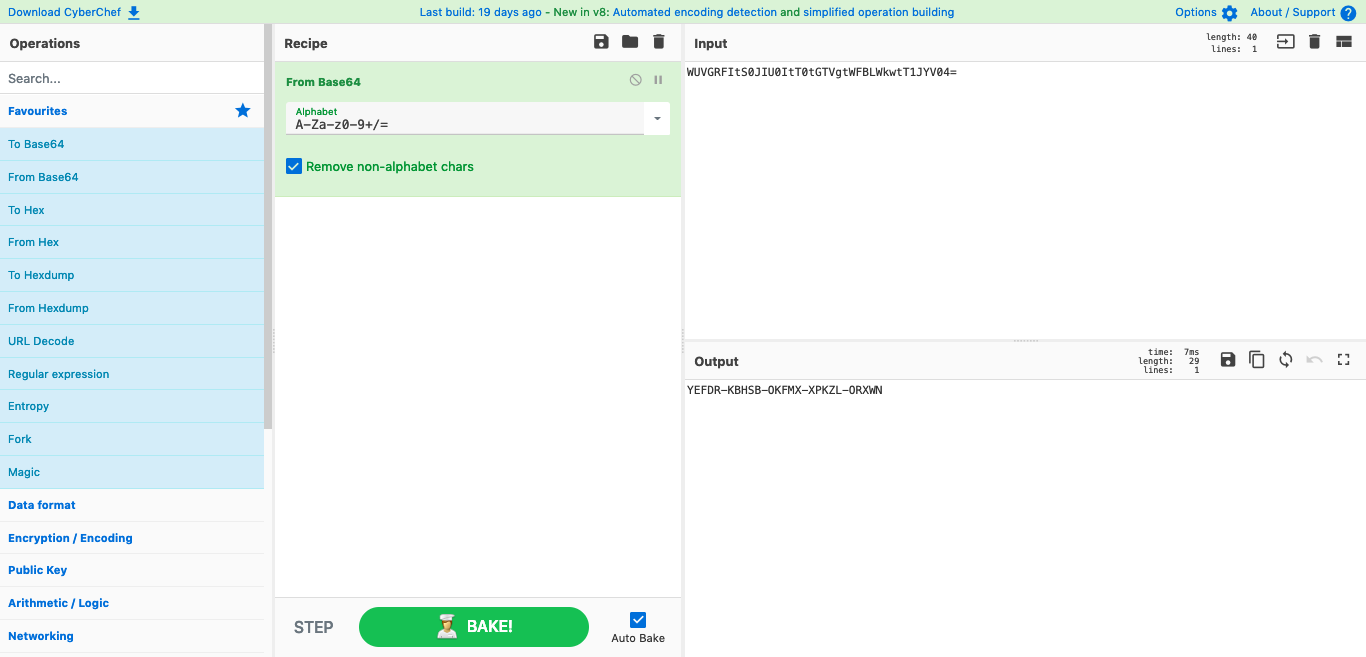 Screenshot of CyberChef decrpyting base64 text.
Screenshot of CyberChef decrpyting base64 text.
Now all that is left is to go back to hackthebox.eu/invite and type the invite code in and you’re in.
CONCLUSION
The amount of learning content this week has been dramatically reduce due to nearing the conclusion of this subject. The reduction of content is appreciated as week 3 was very intensive and cause me to burn out. The week allowed me to recouperate and to review my experience overlooking the highlights, lowlights and insights of the learning cyber security.