Cyber Security: Offensive Mindset - Major Portfolio
INTRODUCTION
About Me.
I am Andre Pagala with a passion and seeking a career in Cyber Security. My degree is a Bachelor of Engineering (Honours) in Software Engineering and Bachelor of International Studies in Japanese. I have strong passion and self-motivated drive to study Cyber Security with protecting mine and everyone’s digital identify in the digital world we are creating today and for the future generations. With technical skills developed in programming I have the capabilities and dedication to further pursue a field that can change society interact with each other in the future.
SLO 1 - Engage with stakeholders to identify a problem
The problem in the 21st century is that the social paradigm has shifted too fast with the exponential expansion of technology and the booming multi trillion business it brings to every country. A society where we have the access to information to anywhere in point in world in the palm of our hands individuals have lost their sense of identity and belonging to a community due the amount of information freely given on the world-wide web. This mass production of data has become a business for major of the top 100 companies’ technologies selling your identity to more companies that will target you based off what individuals have unknowingly put out on the web. This dataset can in form of data scraping from social medias websites or illegally practices such as using vulnerabilities of software to use exploitation to extract unauthorised data.
For an individual to exist in world shaped by technology, how do you protect yourself from yourself and others and why should one care. This is overarching problem statement for myself to enter and complete a Summer Studio in Cyber Security. My knowledge in cyber security is limited and basic which is the reason why am I self-motivated and driven to learn more about how we can make the future as a safe place for everyone.
Throughout the 4 weeks of cyber security, the studio had engaged with 3 teams of cyber security expects from world leading companies of cyber security. The second week, the first of 3 talks, was led by Robert Mitchell, a security engineering whom works at Gilad, explored history of cyber security and why it impossible to fix every bug and vulnerability that had, has and will ever exist. The one of main reason nothing will be 100% secure is that security had always been a second thought when developing a software tool. This demonstrates that companies back since the 1980s will allocate a small budget to security thus making networks and system vulnerable to attacks.
The second team of cyber security professional that presented are called a red team from Deloitte, a major consulting firm. In world of cyber security, red team stems from the military strategic plan where a team of attackers called the red team would have penetrate the systems and network of a team called the blue team whom would will have to defend against any threats. This training exercises help efficiently train and prepares in sudden case of a cyber-attack. The aim is make the blue team significantly effective against the world of hackers who may be motivated to cause harm to an individual or organisation. Organisations such as Deloitte that offers one of the largest professional services for consulting have begun to identify cyber security as important aspect of their business model. Having a red team of security consultants helps build trust and reputation of the company between their clients. Security consultants are required to help identify and calculate the financial risk of cyber-attacks and vulnerabilities that may compromise the company. Web application testing is one of the main areas Deloitte have dedicated their effort to help secure their assets, mitigate and reduce amount of impact that can be caused.
The third speaker Ruben is a security engineer at Symantec, one of the biggest provider of security solutions, explained the importance of learning reverse engineering. With current growth technology, it was identified and highlighted a programming should be a national STEM (software, technology, engineering and mathematics) subject included into primary and high school curriculum. Basic understanding and literacy in coding will be an essential life skill that should be learnt during school to bring help raise awareness of the understanding of internet usage and how it can affect your life directly.
SLO 2 - Apply design thinking to respond to a defined or newly identified problem
Tools
Cyber security is the practice of protecting systems, networks and programs from digital or physical attacks. These attacks are aimed to access, change, or destroy valuable data, scamming money from individuals or interrupting the management of a business. It is only through the effective management of cyber security measures organisations can protect themselves from harm. Security professionals uses an large array of tools as each software is usually created to perform a specific task.
Environment
The preferred environment that the industry uses is Kali Linux because it an Unix-based software that many of the open sourced security programs are built and used on. Kali Linux is usually running through a virtual machine software that allows users to take their system and use it any compatible computers. Computers are recommended to have at least 8GB of RAM (Random-access memory) and Intel i5 equivalent CPU (central processing unit).
- Operating system/Distribution
- Kali Linux
- Native
- Virtual Machine
- Virtual Box
- VMWare Workstation Pro
Programs
The shell is a user interface to access the operation system’s services which uses command-line interface (CLI) or graphic user interface (GUI).
- Command Line/Shell
- iTerm2 (Mac OS)
- Terminal (Mac OS)
- bash (Linux)
- Terminator (Linux)
- Ubuntu for windows (Windows)
The studio requires creating a static site to host weekly reflections of our progress during the studio.
- Web Development
- Git
- Hugo
Open-sourced cracking software tool that is used to encode and decode strings usually in the form of encrypted passwords hashed.
- Encoders/Decipher
- Johnny the Ripper
- Hash cat
- Cyber Chef
Networking tools are used to discover and analyse hosts and services on a computer network by sending packets and analysing response. These tools are typically used for gathering intelligence on the services and hosts running on a vulnerable machine.
- Networking
- nap
- net discover
- msfconsole scanners
Web application pentesting includes a vary of tools that is specific created to do a certain job. The example below is to scan and test vulnerabilities found within a web application. Tools like metasploit and hydra can be used to exploit the system and gain user or root privilege.
- Web Application Testing
- Burpsuite
- WPScan
- Metasploit
- Hydra
Security reverse engineering is the process of analysing software systems and programs designed to be extract the design of the program and reconstruct it.
- Reverse Engineering
- Binary Ninja
Intelligence Gathering
Intelligence gathering is the very first stage of process to get the desired outcome a user wants whether is maybe credentials or taking over vulnerable machines using root access. This is point where users must use variety of tools to gather the most amount of relevant information to a vulnerability. Recon consists of using ‘netdiscover’ a tool that searches for IP addresses on a network and ‘nmap’ is a network scanner that discovers hosts and services on a computer network. Finding ip addresses, hosts and its services allows us to decide what path a user can choose.
Using a vulnerable machine who demonstrate the functionality of the netdiscover we can use the command netdiscover. The example using the command netdiscover 192.168.182.0/24 uncovers all the used IP on the network. This allows an user to identify which vulnerable machine there are attacking. Using knowledge from the studio I can identify the default IP addresses 192.168.182.1, 192.168.182.2 & 192.168.182.154 and remaining IP will be questionable addresses to test for the nmap scans.
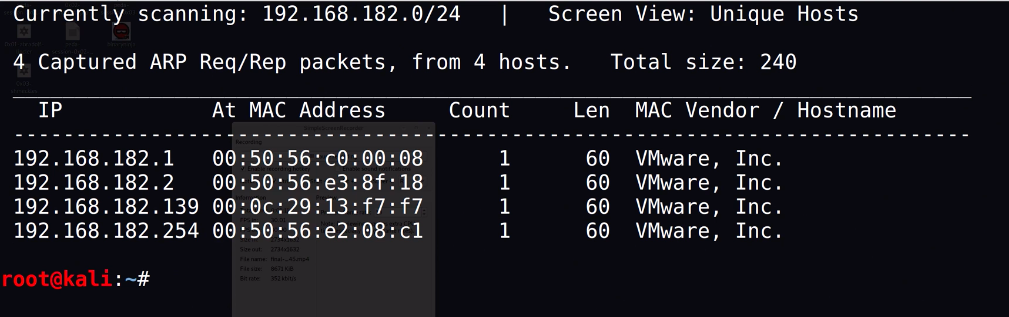 Figure 2.1. Screenshot of using netdiscover on a vulnerable machine.
Figure 2.1. Screenshot of using netdiscover on a vulnerable machine.
Commands on Netdiscover
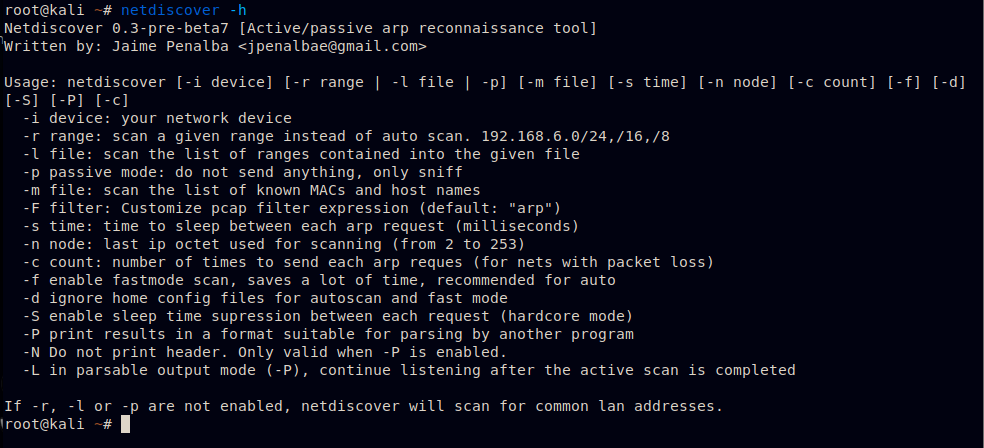 Figure 2.2. Screenshot of available commands on netdiscover.
Figure 2.2. Screenshot of available commands on netdiscover.
Nmap is an extremely powerful network scanner tool is used find to hosts and services running on the network. In the vulnerable machine example below, the tool found any services that was on the given IP address found in the previous method. With intelligence gathering, it often using multiple tools one after another to find clues. In this instance, the nmap -sV 192.168.182.139 has found 3 services running on the ports 21,22 and 80. It is good practice to gather further information what services are running on these ports. If the CTF challenge is about web it’s most likely going to be using port 80 and 21 to get root access as demonstrate in the figure below.
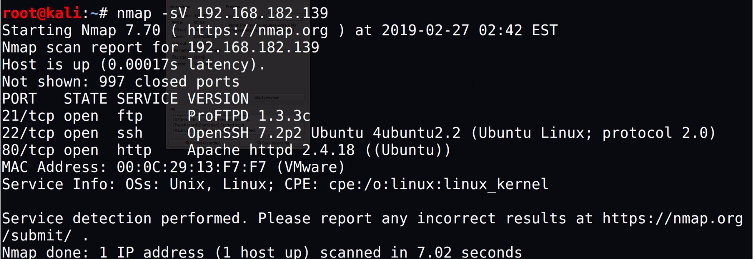 Figure 2.3. Screenshot of using nmap on a vulnerable machine.
Figure 2.3. Screenshot of using nmap on a vulnerable machine.
Commands on Nmap
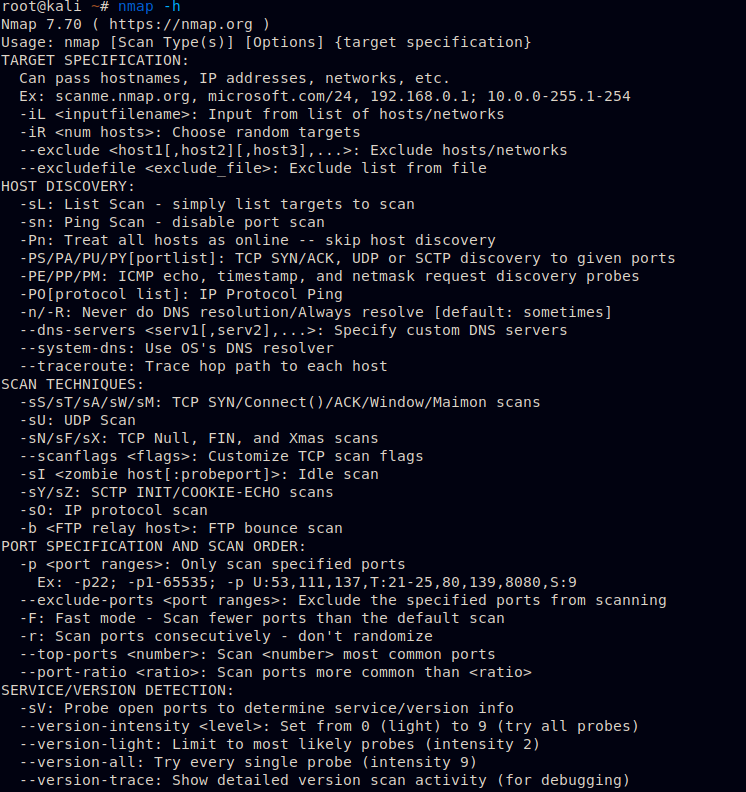 Figure 2.4. Screenshot of available commands nmap.
Figure 2.4. Screenshot of available commands nmap.
Vulnerability Scanning
A vulnerability assessment allows recognising, categorising and characterising the security holes, known as vulnerabilities on computers, networks, software and hardware system. A vulnerability scanner is program that performs scans through networks, computers and application for known vulnerabilities. It is often used to patch out-of-date versions software or used to exploit the weaknesses of dated software. Msfconsole and nikto are vulnerability tools that was used the student to find the exploit.
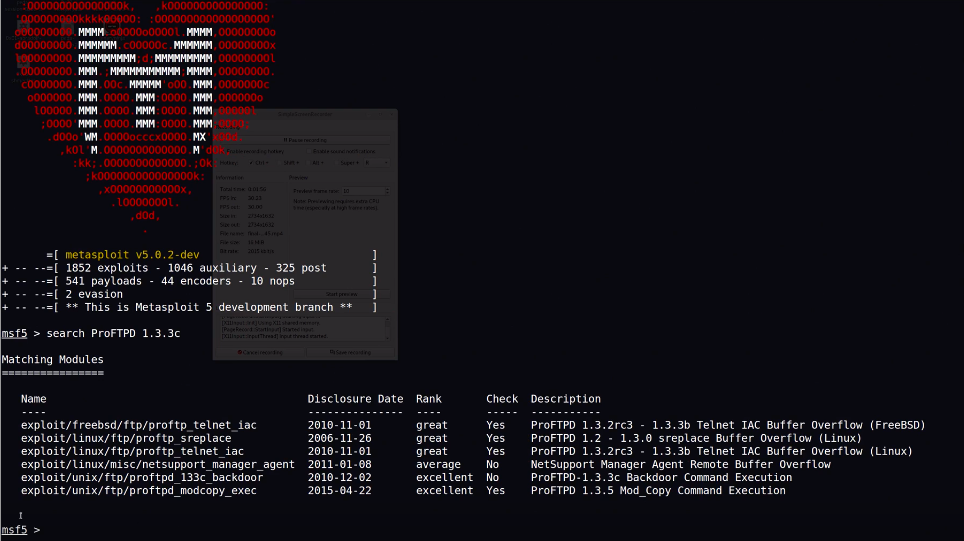 Figure 2.5. Screenshot of msfconsole finding a suitable exploit.
Figure 2.5. Screenshot of msfconsole finding a suitable exploit.
SLO 3 - Apply technical skills to develop, model and/or evaluate design
Learning different types of tools one as time is a great way to understand the process of evaluating how approach a challenge. Acquiring the knowledge of all these tools are to build the foundation of a solution and then slowly transform into a proper exploit that can be applied a similar vulnerability. The main goal learning how to exploit a vulnerability is to gain unauthorised access or compromised the integrity to the network or device.
Exploitation
An exploit is a section of software or sequence of commands and tools to take advantage of a bug or vulnerability in a network or system to cause assess or change data. This results in combination of exploits using reverse shells to gain root access of a network or through privilege escalation. However, the vender of the code will typically rollout a fix, or patch in the next update in response against attacks. Owners of these systems with vulnerable software will response by obtaining the patch as soon as possible to mitigate the chance of an attack. Failure to install a patch within a given time-lapse increase the chance of a cyber-attack on a computer using an exploit and possibility cause a security breach.
Some of the most common exploits are SQL injection attacks, cross-sites scripting and cross-site request forgery, as well as abusing broken authentication code or security misconfigurations. Computer exploits can be classified by the expected result of an attack, such as denial of service, remote code execution, privilege escalation, malware delivery or other malicious targets. Exploits can also be characterised by the type of vulnerability being exploited including buffer overflow, code injection, backdoor and input validations.
For web application, the OWASP Top 10 is a powerful awareness document for web application security. It displays the expansive census about the most critical security risk to web applications. Companies are recommended to adopt the awareness of the document to start the process of securing web application reduce the impact of this risks.
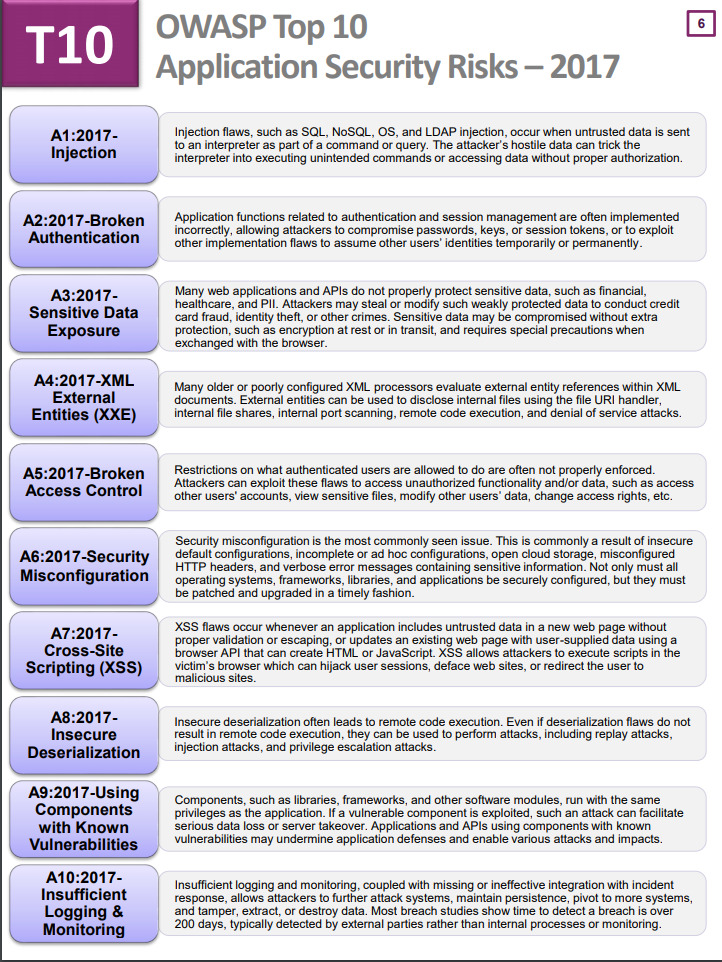 Figure 3.1. Table of the OWASP Top 10 from the documentation.
Figure 3.1. Table of the OWASP Top 10 from the documentation.
An example of using a exploit in the HTTP/80 protocol is to install a reverse shell. In this particular example as displayed in the figure below is using a .php reverse shell from the internet in hopes to gain access to the network directory system.
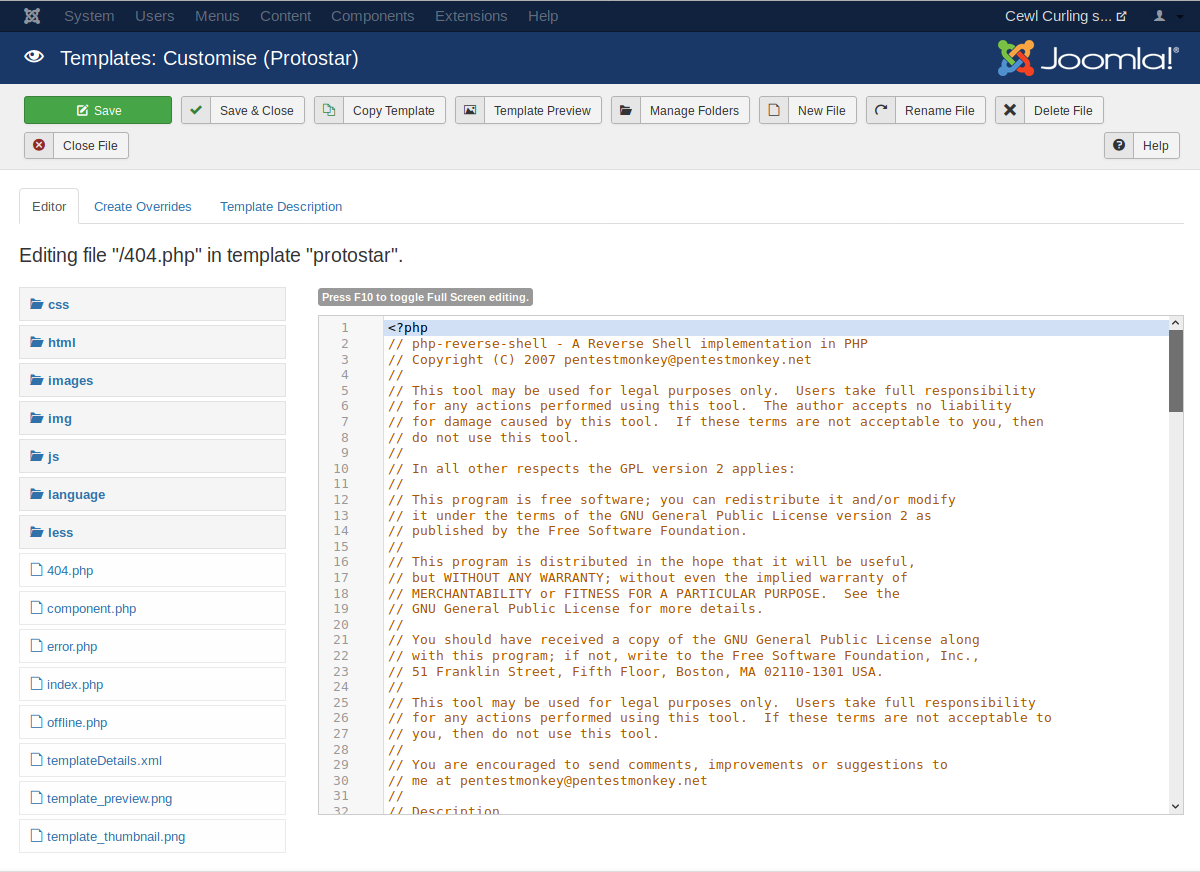 Figure 3.2. Screenshot of msfconsole finding a suitable exploit.
Figure 3.2. Screenshot of msfconsole finding a suitable exploit.
Following the successful connection to the network directory network on bash or through a exploit found msfconsole or metasploit, a user can use privilege escalation if they are have root access to the system to further gain full control of it. The example below demonstrates continuation of root the machine using a msfconsole exploit from the example in figure 2.6. Choosing the backdoor as the exploit and configuring the setting correctly yield root access. Root access allows the user freewill to do whatever their intention is with the network or system. Usually gaining root access helps users to find hidden usernames and password in passwd and shadow file which can be to exploit other software.
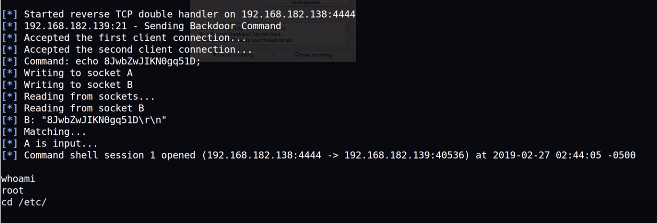 Figure 3.3. Screenshot of msfconsole finding a suitable exploit.
Figure 3.3. Screenshot of msfconsole finding a suitable exploit.
SLO 4 - Demonstrate effective collaboration and communication skills
I thoroughly enjoyed the group presentations that this subject required that forced us focus and work together. Although I had had bad experience with presentations due my nervousness and anxiety speaking in front of a crowd, I enjoyed learning about content and discussing it with fellow peers. This type of group project was extremely rewarding that allow me to further improve my soft skills especially communication.
 Figure 4.1. Three groups that were made during the studio.
Figure 4.1. Three groups that were made during the studio.
Mitigation
Mitigating issues is exceptionally hard to think of solutions that is catered for a situation. In web application security, the OWASP (Open Web Application Security Project) have been continually publishing reports and articles free to public to help educate organisations of the top 10 risks to web applications. The OWASP organisation also have a ‘Top Ten Proactive Controls’ a list of security techniques and best practices enterprises should practice mitigating majority of the most prevalent and exploitable vulnerabilities found in today’s web applications.
In order of importance (OWASP Top Ten Proactive Controls 2018):
 Figure 4.2. Logo and title of OWASP Top Ten Proactive Controls 2018
Figure 4.2. Logo and title of OWASP Top Ten Proactive Controls 2018
- Define Security Requirements
- Leverage Security Frameworks and Libraries
- Secure Database Access
- Encode and Escape Data
- Validate All Inputs
- Implement Digital identity
- Enforce Access Controls
- Protect Data Everywhere
- Implement Security Logging and Monitoring
- Handle All Errors and Exceptions
Implementing the OWASP’s list will help reduce the vulnerabilities and lower development time and cost to minister the number of coding errors made during development. In addition, good coding practices will reduce the quantity of easy attack vectors for hackers. The tenth proactive control essential in understanding good coding practices as developers how should program for all possible edge case scenario which leaves nothing to be exploitable by hackers.
In the last 5 years, policies and guidelines for better and stronger passwords have been increasing due to escalation of different data breaches that have compromised over 1 billion accounts. Google and thousands of organisations have follow through by using 2 step verification process that is linked to a device to receive another key to attempt to login. This authentication system uses Time-based One-time-Password Algorithm and HMAC-based One-time Password Algorithm and is a great security measure. Allowing the use of more passwords decrease the number of brute forced logins that is only successful using common words and usually 1 password.
SLO 5 - Conduct critical self and peer review and performance evaluation
The studio was extremely engaging and required an unexpected amount of dedication and time for me to be satisfied when this concludes. For the past 2 years, I have been a university, this is only of few the subjects that I have put in 100% of my effort and 100% time into. It is also the only subject I am being apart where 100% of the students are just as excited and engaged as you are learning about the subject. Without tutors Larry, Darsh, Luke and Jai the transparency and fantastic learning experience will be nothing without them. The high level active of engagements they do give to us is important and valuable as student. There is not more demoralising learning something for nothing, so it was incredible to have polished subject that majority of its content is transferable to real life industry experience.
Executive Report
Cyber security main objective is preventing access of specific areas of a network and/or system to certain amount or specific individuals. However as discussed before it is impossible to find and fix all bugs and vulnerabilities. As the world continues to develop more software there will be an endless supply of jobs for security professionals. Using exploitation on vulnerable systems on real services and networks can cause disruptions of systems and loss of profit of a company. Furthermore, if services are used for aid or city management are down, this can potentially lead to mass chaos and loss of death. As the name of the studio suggests, ‘An Offensive Mindset’, explores the ideology of rejecting manufacturing of fabricated digital identities shaped by the mass intelligence gathering of companies and protecting your personal identity against threats that may have a life changing impact.
The goal of a business is creating profit and increase capital through selling a service such selling private data however there is currently a need for security professional in every business demonstrated by the amount of bug bounty platforms rising and insurances for against data breaches. Individuals must understand and follow simple data security rules like choosing strong password, storing them correctly, backing up data and identifying risks. In addition, it is only through the awareness and training of introducing cyber security subjects into the primary and high school STEM curriculum that individuals can develop an offensive mind-set to be identity and problem solve security threats and vulnerabilities more effectively and quickly.
CONCLUSION
Overall this studio effective train me into a different mind-set of requiring my passion of cyber security to creative think of solutions. It has been an extremely beneficial use of my time dedicating most of my time researching and doing cyber security. Comparing my progress from the start to end of studio I have grown significantly however I believe this is just the start of my journey in career in cyber security.
During this studio, I set out a goal getting a job in cyber security and I achieve half of this goal. I was fortunate to get an interview for the UTS Junior Security Analyst role however that position was achieved by another student in studio, Max Caminer. The interview has shown me I have still have years to go learning about networking and information security however with my resilience I will keep applying for relevant position until I have reach my goal.
I am highly fortunate to be a part of this studio as it was a great and fun opportunity for me to learn cyber security and get it credited on my academic transcript. My interest into cyber security will continue to advance into participating in regular CTFs, attending cyber community events like SecTalks and UTS Cyber Security Society socials.
 Figure 6.1. Thanks to all the kind folks I have met during the studio, I hope we have opportunity to meet again.
Figure 6.1. Thanks to all the kind folks I have met during the studio, I hope we have opportunity to meet again.
 Figure 6.2. Thank you to all the other students from the other studio who came to our studio and saw our presentations
Figure 6.2. Thank you to all the other students from the other studio who came to our studio and saw our presentations
Bibliography
Cisco n.d., ‘What is Cybersecurity?, CISCO, viewed 3rd March 2019, http://www.cisco.com/c/en/us/products/security/what-is-cybersecurity.html
GitHub 2019, ‘Awesome Penetration Testing’, enaqx, viewed 3rd March 2019, https://github.com/enaqx/awesome-pentest
Techgyo 2018, ‘How to Mitigate Web Application Vulnerabilites and Enhance Security’, Editorial Team, viewed 3rd March 2019, https://techgyo.com/how-to-mitigate-web-application-vulnerabilities-and-enhance-security
SearchSecurity 2014, ‘How can the OWASP Top Ten reduce Web Application vulnerabilities?’, Michael Cobb, viewed 3rd March 2019, https://searchsecurtiy.techtarget.com/answer/How-can-the-OWASP-Top-Ten-reduce-Web-application-vulnerabilities
OWASP 2018, ‘OWASP Top 10 Proactive Controls 2018’, OWASP, viewed 3rd March 2019, https://www.owaps.org/index.php/OWASP_Proactive_Controls
Webopedia n.d., ‘Security Exploit’, Forrest Stroud, viewed 3rd March 2019, https://www.webopedia.com/TERM/S/security_exploit.html
SearchSecurity n.d., ‘computer exploit’, Margaret Rouse, viewed 3rd March 2019, https://searchsecurity.techtarget.com/defintion/exploit
OWASP 2017, ‘OWASP Top Ten Project’, OWASP, viewed 3rd March 2019, https://www.owasp.org/index.php/Category:OWASP_Top_Ten_Projectai